$16 Million Fine For T-Mobile: A Three-Year Data Breach Investigation
Table of Contents
The Timeline of the T-Mobile Data Breach Investigation
The T-Mobile data breach investigation unfolded over a protracted period, marked by several key milestones. Understanding this timeline offers valuable insights into the complexities of responding to and resolving large-scale cybersecurity incidents. Effective cybersecurity incident response requires swift action and meticulous documentation. The T-Mobile case serves as a cautionary tale for how a delayed or inadequate response can lead to substantial financial repercussions.
- [Date]: Initial reports of suspicious activity emerged within T-Mobile's systems, suggesting a potential compromise of customer data. These early warnings often go unnoticed or are dismissed, highlighting the importance of proactive monitoring and threat detection systems.
- [Date]: T-Mobile launched an internal investigation, though the exact start date remains unclear. The delay in acknowledging and addressing the issue exacerbated the problem and likely contributed to the extent of the breach. This underscores the necessity for rapid incident response protocols.
- [Date]: The full extent of the data breach began to surface, revealing a massive compromise of customer data. The delay in disclosure further complicated matters and allowed the breach to persist longer than necessary.
- [Date]: Regulatory agencies, notably the Federal Trade Commission (FTC), initiated their own investigations into T-Mobile's security practices and handling of the data breach. The involvement of regulators significantly increased the pressure on T-Mobile to address the issue.
- [Date]: A settlement agreement was reached between T-Mobile and the regulatory bodies involved. This agreement included a substantial fine, reflecting the severity of the breach and T-Mobile's shortcomings in data security.
- [Date]: The $16 million fine was officially imposed on T-Mobile, marking the conclusion of the long investigation and a significant financial penalty for the company's negligence.
The Nature and Scope of the Data Breach
The T-Mobile data breach was extensive, exposing sensitive personal information of millions of customers. This compromised data presented significant risks, impacting not only T-Mobile's reputation but also the financial well-being and security of its customers. Understanding the nature and scope of such breaches is critical for implementing effective preventative measures.
- Number of affected customers: While the exact number varies depending on the report, millions of T-Mobile customers were affected. This demonstrates the far-reaching impact of a single security failure.
- Types of data compromised: The breach included Personally Identifiable Information (PII) such as names, addresses, Social Security numbers, driver's license numbers, and financial information. The exposure of this sensitive data posed an elevated risk of identity theft and financial fraud for affected customers.
- Potential consequences for affected customers: The consequences for affected customers included identity theft, fraudulent credit card applications, and financial losses. This highlights the devastating personal consequences of data breaches.
The Regulatory Response and Penalties
The regulatory response to the T-Mobile data breach underscores the seriousness of the incident and the legal obligations companies have to protect customer data. The $16 million fine reflects the magnitude of the violations and the need for stronger accountability in the realm of data security.
- Specific regulations violated: T-Mobile violated various federal and state laws related to data security and consumer protection. These violations included failures to implement adequate security measures to protect sensitive customer data and to comply with notification requirements in the event of a data breach.
- Actions taken by regulatory bodies: The FTC launched a comprehensive investigation into the T-Mobile data breach, scrutinizing the company's security practices and its response to the incident. This investigation led to the settlement and the imposition of the $16 million fine.
- Details of the settlement agreement: The settlement agreement likely included not only the $16 million fine but also mandates for T-Mobile to improve its data security practices and implement stricter measures to prevent future breaches. This often includes mandated independent security audits and increased investment in security infrastructure.
- Breakdown of the $16 million fine: While the exact breakdown isn’t publicly available, it’s likely a combination of civil penalties and restitution to affected consumers.
Lessons Learned and Best Practices for Data Security
The T-Mobile data breach serves as a cautionary tale, offering valuable lessons for businesses and organizations of all sizes. Proactive measures and a robust security posture are essential to mitigating the risk of costly and damaging data breaches.
- Importance of robust cybersecurity infrastructure: Investing in a strong cybersecurity infrastructure, including firewalls, intrusion detection systems, and data loss prevention (DLP) tools, is crucial for protecting sensitive data.
- Need for regular security audits and penetration testing: Regular security assessments and penetration testing can identify vulnerabilities and weaknesses in an organization's security systems before they can be exploited by malicious actors.
- Employee training on data security protocols: Educating employees about data security best practices and implementing strong security awareness training programs can significantly reduce the risk of human error, a frequent cause of data breaches.
- Importance of incident response planning: Having a well-defined incident response plan in place is crucial for effectively managing and mitigating the impact of a data breach. This plan should outline clear procedures for detection, containment, eradication, recovery, and post-incident activity.
Conclusion
The $16 million fine imposed on T-Mobile for its three-year data breach investigation serves as a potent example of the high cost of inadequate data security. This case highlights the importance of proactive security measures, robust incident response plans, and compliance with relevant data protection regulations. Failing to prioritize cybersecurity can lead to significant financial penalties, reputational damage, and legal repercussions. Learn more about protecting your business from costly data breaches. Explore best practices for data security and avoid the consequences of a major security lapse. Consider the T-Mobile data breach case study a critical lesson in strengthening your cybersecurity posture.

Featured Posts
-
 Jazz Cash K Trade Collaboration Making Stock Investment Accessible To All
May 09, 2025
Jazz Cash K Trade Collaboration Making Stock Investment Accessible To All
May 09, 2025 -
 The Bitcoin Rebound Opportunities And Risks For Investors
May 09, 2025
The Bitcoin Rebound Opportunities And Risks For Investors
May 09, 2025 -
 1509
May 09, 2025
1509
May 09, 2025 -
 Bondi Announces Record Breaking Fentanyl Seizure In Us History
May 09, 2025
Bondi Announces Record Breaking Fentanyl Seizure In Us History
May 09, 2025 -
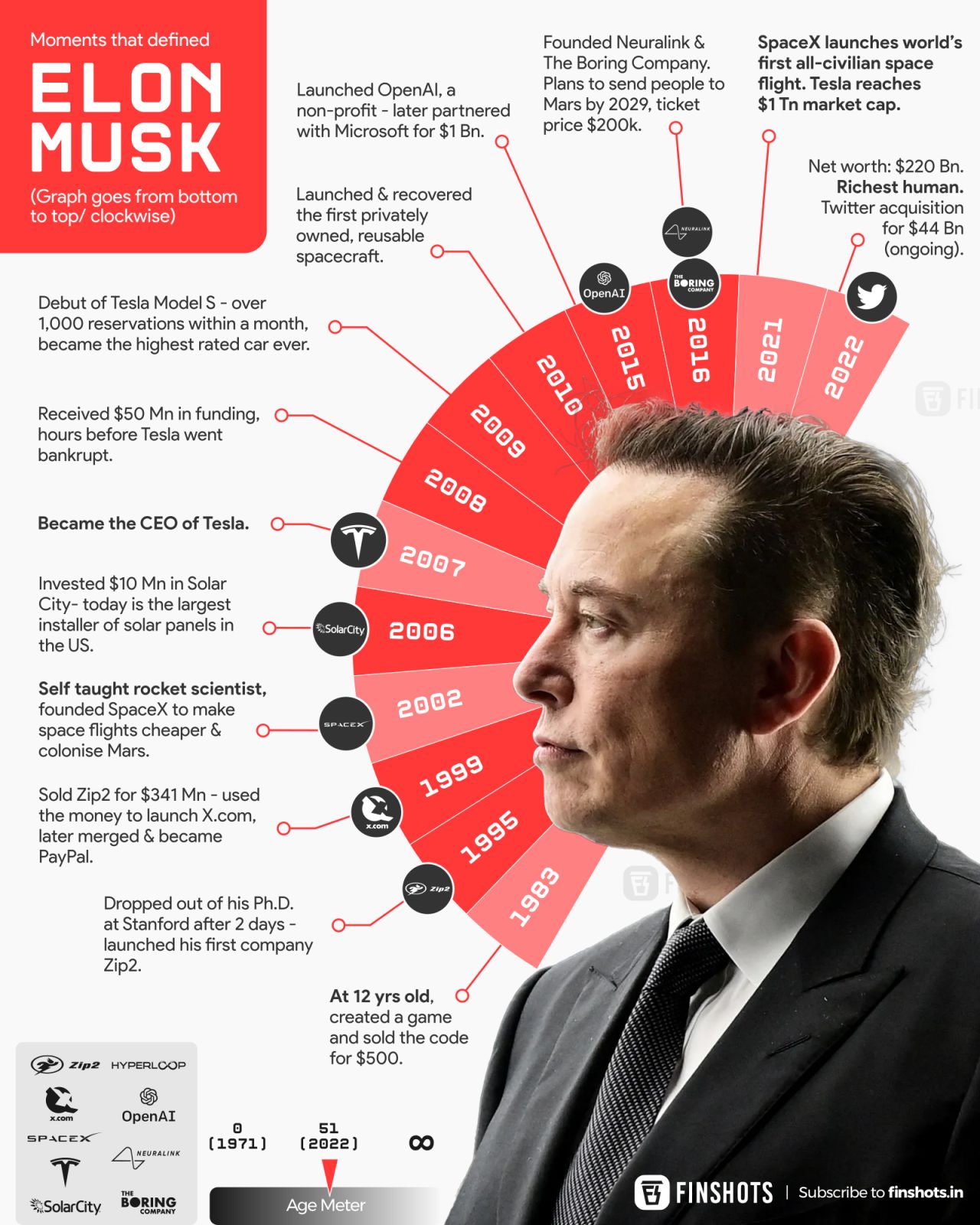 Understanding Elon Musks Financial Journey Strategies And Investments
May 09, 2025
Understanding Elon Musks Financial Journey Strategies And Investments
May 09, 2025
