Deepfake Detection Foiled: Cybersecurity Expert's Clever Technique
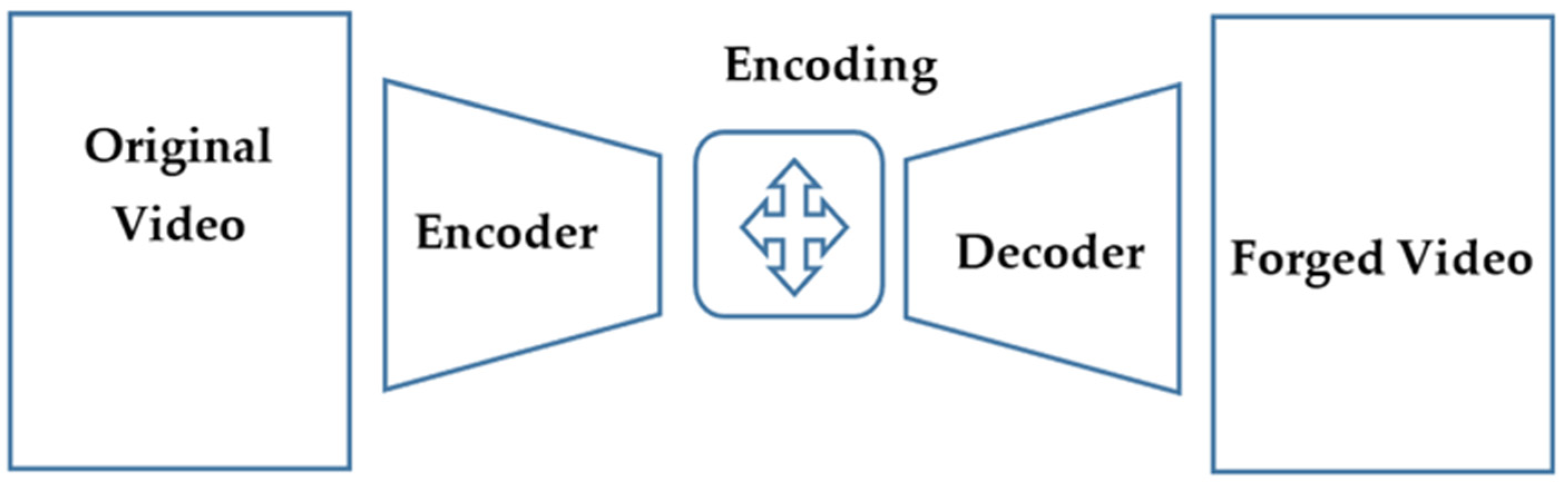
Table of Contents
The Existing Landscape of Deepfake Detection
Current deepfake detection methods rely on identifying inconsistencies within the video or audio. These inconsistencies often stem from imperfections in the deepfake creation process. Techniques include analyzing inconsistencies in blinking patterns – real human blinks are subtly different from those generated by AI – subtle artifacts left behind by the deepfake generation algorithm, and inconsistencies in lighting and shadow across the subject's face.
- Frequency analysis methods: These techniques analyze the frequency components of audio and video signals to identify anomalies indicative of deepfakes.
- AI-based detection tools: Machine learning models are trained on large datasets of real and fake videos to learn distinguishing features. These tools often utilize convolutional neural networks (CNNs) to analyze visual features and recurrent neural networks (RNNs) for temporal analysis.
- Limitations of current techniques: Existing methods are often computationally expensive, requiring significant processing power. Furthermore, they are susceptible to adversarial attacks, meaning that relatively minor adjustments to the deepfake can render these detection techniques ineffective. Advanced deepfakes are increasingly difficult to distinguish from genuine media.
The Cybersecurity Expert's Novel Technique
A cybersecurity expert has recently developed a novel technique that effectively bypasses many existing deepfake detection mechanisms. This method focuses on manipulating metadata and introducing almost imperceptible alterations to the video's temporal characteristics, effectively fooling detection algorithms. While the specifics of the technique remain confidential to prevent its misuse, the core concept involves exploiting vulnerabilities in the way current detection software analyzes video data.
- Specific steps involved in the technique: The technique involves manipulating metadata embedded within the video file and making subtle adjustments to frame rates and timestamps. These alterations are often too small to be detected by the human eye.
- The types of deepfakes it successfully bypasses: The technique has proven effective against several state-of-the-art deepfake detection algorithms, including those utilizing frequency analysis, AI-based classification, and even those focusing on subtle visual inconsistencies.
- The platforms or tools used in the process: The expert utilized commonly available video editing software and readily accessible metadata manipulation tools, highlighting the accessibility of the technique to those with malicious intent.
Exploiting Temporal Inconsistencies in Video Analysis
This technique cleverly exploits the limitations of temporal video analysis within deepfake detection software. By making micro-adjustments to the video's frame rate and timestamp data, the expert introduced inconsistencies that are easily overlooked by human observers but significantly alter the results of automated detection algorithms.
- Examples of subtle changes: These include minute adjustments to frame rates, introducing very slight variations in timestamp accuracy, and carefully placed micro-stutters within the video.
- How these changes affect detection algorithms' accuracy: These subtle alterations disrupt the algorithms' ability to analyze the video's temporal consistency, leading to false negatives and misidentification of the video as genuine.
- The technical details of the manipulation: The manipulation is performed at a low level, subtly altering the fundamental timing information of the video file, causing detection algorithms to misinterpret the data.
Implications for the Future of Deepfake Detection
The successful application of this new technique has significant implications for the future of deepfake detection research. It underscores the urgent need for more robust and adaptive detection methods that go beyond simple visual and audio analysis.
- The need for more robust and adaptive detection methods: Future deepfake detection methods will need to incorporate more sophisticated analysis techniques, potentially including blockchain-based verification methods and more robust examination of metadata integrity.
- The potential for a new arms race between deepfake creators and detection experts: This discovery will likely fuel an ongoing arms race between those who create deepfakes and those who attempt to detect them, leading to an ongoing cycle of innovation and counter-innovation.
- The importance of improving digital literacy to recognize potentially manipulated media: Public education is critical in combating the spread of deepfakes. Individuals need to be equipped with the skills to critically assess online media and identify potential signs of manipulation.
Practical Considerations and Mitigation Strategies
Addressing the deepfake threat requires a multi-pronged approach involving technological advancements, public awareness, and policy changes.
- Increased media literacy education for the public: Educating the public on how to identify deepfakes and evaluate the credibility of online information is crucial.
- Development of more sophisticated deepfake detection tools: Investment in research and development is critical to creating more robust and resilient deepfake detection algorithms.
- Strengthening authentication and verification processes for online content: Platforms and organizations should prioritize strengthening their authentication and verification processes to ensure the authenticity of online content.
Conclusion:
The discovery of this novel technique highlights the ongoing challenge of combating the spread of deepfakes. While current deepfake detection methods provide a level of protection, they are not foolproof. The cybersecurity expert's success underscores the urgent need for continuous innovation and development in the field of deepfake detection. We must invest in more resilient and adaptive technologies, while simultaneously raising public awareness to combat the malicious use of this technology. Stay informed about the latest advancements in deepfake detection and adopt proactive strategies to protect yourself from misinformation and cyber threats. Learning to effectively utilize deepfake detection software is now more vital than ever before.

Featured Posts
-
 Investing In The Future Identifying The Countrys Top Business Locations
May 17, 2025
Investing In The Future Identifying The Countrys Top Business Locations
May 17, 2025 -
 The Evolving Microsoft Surface Lineup Discontinued Products And Future Directions
May 17, 2025
The Evolving Microsoft Surface Lineup Discontinued Products And Future Directions
May 17, 2025 -
 Analyzing Trumps Bromance With Arab Leaders A Look At The Rhetoric And Reality
May 17, 2025
Analyzing Trumps Bromance With Arab Leaders A Look At The Rhetoric And Reality
May 17, 2025 -
 Modular Homes A Potential Solution To Canadas Housing Challenges
May 17, 2025
Modular Homes A Potential Solution To Canadas Housing Challenges
May 17, 2025 -
 Hudsons Bay Brand Assets Sold To Canadian Tire A 30 Million Transaction
May 17, 2025
Hudsons Bay Brand Assets Sold To Canadian Tire A 30 Million Transaction
May 17, 2025
Latest Posts
-
 Gncc Mx Sx Flat Track Enduro Your Source For Moto News
May 17, 2025
Gncc Mx Sx Flat Track Enduro Your Source For Moto News
May 17, 2025 -
 Overcoming Adversity Josh Cavallos Journey And Legacy
May 17, 2025
Overcoming Adversity Josh Cavallos Journey And Legacy
May 17, 2025 -
 Moto News Gncc Mx Sx Flat Track And Enduro Racing Updates
May 17, 2025
Moto News Gncc Mx Sx Flat Track And Enduro Racing Updates
May 17, 2025 -
 The Impact Of Josh Cavallos Public Coming Out
May 17, 2025
The Impact Of Josh Cavallos Public Coming Out
May 17, 2025 -
 How Josh Cavallo Is Changing Football With His Story
May 17, 2025
How Josh Cavallo Is Changing Football With His Story
May 17, 2025
