Exec Office365 Breaches Net Millions For Crook, Feds Say

Table of Contents
The Scale of the Office365 Breach and its Impact
The sheer scale of this recent Office365 breach is staggering. Reports indicate that criminals netted millions of dollars, exploiting vulnerabilities in executive accounts to access sensitive data. While the exact number of compromised accounts remains undisclosed for investigative reasons, the financial impact on affected businesses is significant. The breach compromised a variety of sensitive data, including:
- Financial records: Criminals likely gained access to bank account details, transaction histories, and confidential financial reports.
- Intellectual property: Trade secrets, proprietary designs, and research data could have been stolen, leading to significant competitive disadvantage.
- Sensitive communications: Confidential emails, strategic plans, and sensitive negotiations were likely compromised, potentially leading to reputational damage and legal issues.
The consequences extend far beyond immediate financial losses. The impact includes:
- High financial impact on businesses: Direct financial losses from theft, plus the costs of investigation, remediation, and legal fees.
- Reputational damage to affected companies: Loss of trust from clients, partners, and investors, impacting future business opportunities.
- Potential legal ramifications and regulatory fines: Non-compliance with data protection regulations like GDPR can result in substantial penalties.
- Loss of customer trust and market share: A data breach can erode customer confidence, driving customers to competitors.
Common Methods Used in Office365 Breaches
Cybercriminals employ various sophisticated methods to breach Office365 accounts. Some of the most prevalent attack vectors include:
- Phishing: Criminals send deceptive emails mimicking legitimate communications, tricking users into revealing their credentials. These emails often appear to be from trusted sources, creating a sense of urgency or offering enticing rewards.
- Spear phishing: This is a more targeted form of phishing, where attackers specifically target high-profile executives with personalized emails designed to exploit their knowledge and trust within the organization.
- Credential stuffing: Attackers use stolen usernames and passwords obtained from other data breaches to attempt to access Office365 accounts. They leverage automated tools to test combinations until they find a successful login.
- Malware: Malicious software, often delivered through phishing emails or infected attachments, can compromise devices and grant attackers access to Office365 accounts. This malware can operate silently, stealing credentials and data without the user's knowledge.
Understanding these tactics is crucial in developing effective preventive measures.
Strengthening Office365 Security: Best Practices and Prevention Strategies
Protecting your organization from Office365 breaches requires a multi-layered approach encompassing technology and user education. Here are some vital strategies:
- Implement MFA for all accounts: Multi-factor authentication adds an extra layer of security, requiring users to verify their identity through multiple methods (e.g., password, one-time code, biometric scan).
- Regular security awareness training for employees: Educate employees on identifying and avoiding phishing emails, recognizing malicious links, and practicing good password hygiene.
- Use advanced threat protection features: Microsoft 365 offers advanced threat protection tools that can detect and block malicious emails and attachments before they reach users' inboxes.
- Employ strong password policies: Enforce the use of complex, unique passwords, and encourage regular password changes. Consider using a password manager to simplify this process.
- Regular software updates and patching: Keep all software, including Office365 applications and operating systems, updated with the latest security patches to address known vulnerabilities.
- Conduct regular security audits: Regularly assess your Office365 security posture to identify weaknesses and vulnerabilities. Consider engaging a cybersecurity professional for penetration testing to simulate real-world attacks.
The Role of Law Enforcement and Legal Implications
Federal investigations into large-scale Office365 breaches are becoming increasingly common. These investigations aim to identify and prosecute the perpetrators, recovering stolen funds and disrupting criminal networks. Organizations themselves face legal responsibilities regarding data protection, including:
- Federal investigation into the cybercrime: Law enforcement agencies actively investigate these breaches, leading to potential arrests and prosecutions.
- Potential legal repercussions for perpetrators: Severe penalties, including hefty fines and imprisonment, await those found guilty of cybercrimes.
- Compliance with data breach notification laws: Organizations are legally obligated to notify affected individuals and authorities of data breaches under various regulations.
- Importance of incident response planning: A well-defined incident response plan is crucial for minimizing the damage and ensuring swift recovery in the event of a breach.
Conclusion:
The recent Office365 breach, resulting in millions of dollars in losses, serves as a stark reminder of the vulnerability of even the most sophisticated organizations to cyber threats. This incident underscores the critical need for proactive and comprehensive cybersecurity strategies. Don't let your organization become the next victim. Strengthen your Office365 security today by implementing robust security measures and protecting your valuable data from potential Office365 breaches. Invest in security training, multi-factor authentication, and advanced threat protection to safeguard your business from financial and reputational damage. Prioritize your Office365 security now.

Featured Posts
-
 Renee Rapp Shades Sex Lives Of College Girls In New Song Leave Me Alone
May 27, 2025
Renee Rapp Shades Sex Lives Of College Girls In New Song Leave Me Alone
May 27, 2025 -
 Cyril Hanouna Et Le Demenagement De L Ecole De Saint Ouen La Ferme Decision Du Maire
May 27, 2025
Cyril Hanouna Et Le Demenagement De L Ecole De Saint Ouen La Ferme Decision Du Maire
May 27, 2025 -
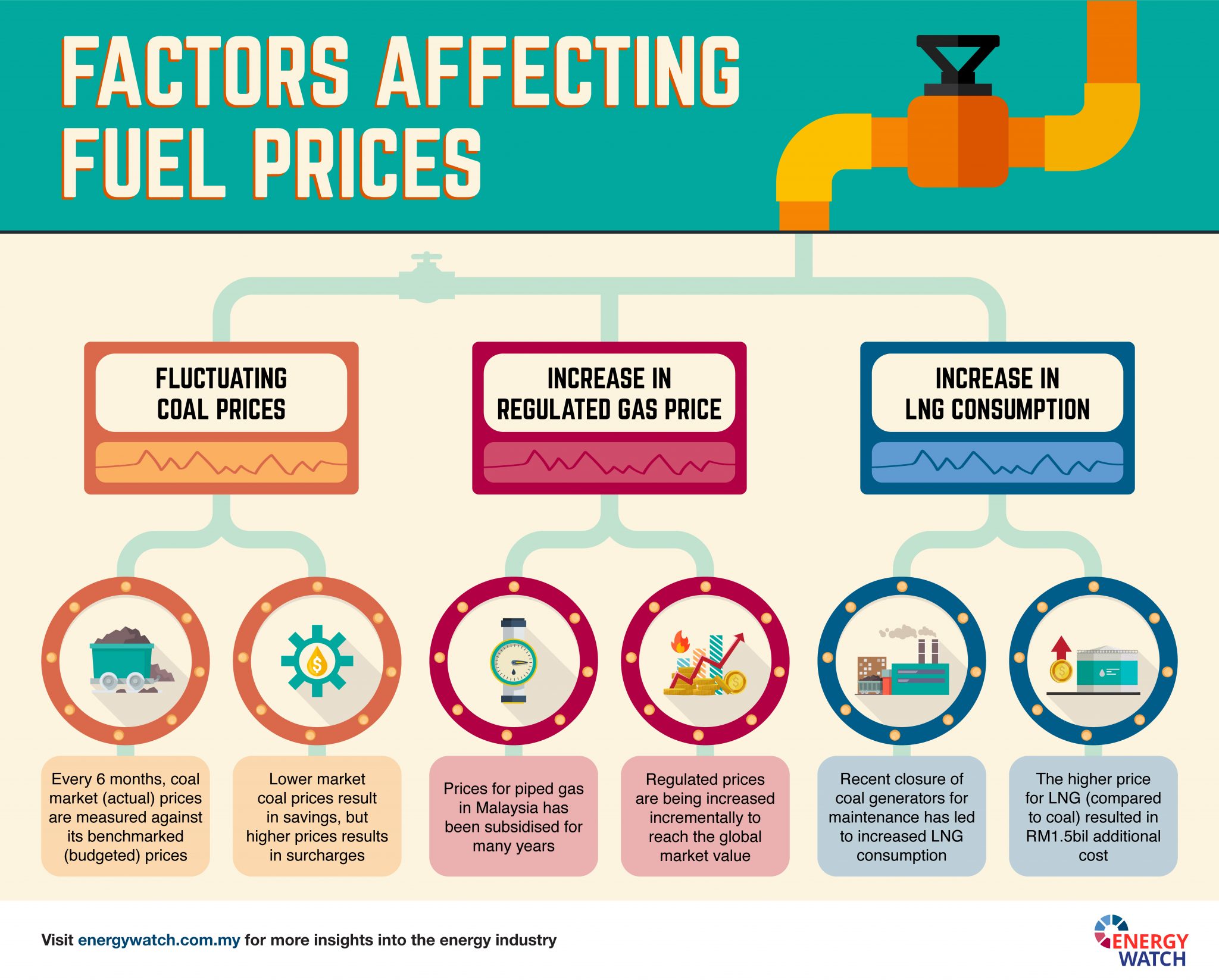 The Right Price For A Watch Factors To Consider
May 27, 2025
The Right Price For A Watch Factors To Consider
May 27, 2025 -
 Galatasarays Pursuit Of Osimhen Ends No Permanent Transfer
May 27, 2025
Galatasarays Pursuit Of Osimhen Ends No Permanent Transfer
May 27, 2025 -
 The New Gucci Re Motion Blue Gg Canvas Handbag 832461 Aaew 34245 May 2025
May 27, 2025
The New Gucci Re Motion Blue Gg Canvas Handbag 832461 Aaew 34245 May 2025
May 27, 2025
Latest Posts
-
 Ipswich Town News Mc Kenna Stellar Tuanzebe Improves Phillips And Cajuste Need Improvement
May 28, 2025
Ipswich Town News Mc Kenna Stellar Tuanzebe Improves Phillips And Cajuste Need Improvement
May 28, 2025 -
 Mc Kennas Rise Phillips And Cajustes Dip Assessing Ipswich Towns Recent Form
May 28, 2025
Mc Kennas Rise Phillips And Cajustes Dip Assessing Ipswich Towns Recent Form
May 28, 2025 -
 Ipswich Town Player Performances Mc Kenna Shines Phillips And Cajuste Struggle
May 28, 2025
Ipswich Town Player Performances Mc Kenna Shines Phillips And Cajuste Struggle
May 28, 2025 -
 Mc Kenna Impresses Tuanzebe Positive Ipswich Towns Week In Review
May 28, 2025
Mc Kenna Impresses Tuanzebe Positive Ipswich Towns Week In Review
May 28, 2025 -
 Indiana Pacers Vs Chicago Bulls Game Time Tv Coverage And Streaming Details March 10
May 28, 2025
Indiana Pacers Vs Chicago Bulls Game Time Tv Coverage And Streaming Details March 10
May 28, 2025
