Federal Investigation Uncovers Millions Lost In Office365 Executive Hacks

Table of Contents
Methods Employed in Office365 Executive Hacks
Hackers employ increasingly sophisticated techniques to breach Office365 security. These attacks often leverage spear phishing attacks, credential theft, and the exploitation of vulnerabilities within Office365 applications. The goal is to gain access to executive accounts, which often provide a gateway to sensitive financial data and internal systems.
- Spear phishing emails: These highly targeted emails mimic legitimate communications, often personalized to trick unsuspecting executives into revealing credentials or downloading malware.
- Credential stuffing: Hackers use stolen usernames and passwords from other data breaches to attempt access to Office365 accounts. Weak passwords make this tactic particularly effective.
- Exploiting Office365 vulnerabilities: Hackers actively search for and exploit known vulnerabilities in Office365 applications and their associated services to gain unauthorized access. This often involves bypassing multi-factor authentication.
- Malware deployment: Once access is gained, hackers may deploy malware to maintain persistent access, steal data, and exfiltrate information undetected.
These methods allow hackers to bypass traditional security measures and gain access to sensitive information, leading to significant financial losses through actions such as wire transfer fraud.
Industries and Executives Targeted by the Hacks
The hacks are not random; they target specific industries and high-value individuals. Sectors such as finance, healthcare, and technology are particularly vulnerable due to the sensitive data they hold and the high financial stakes involved. These are prime targets for targeted attacks on high-value targets.
- Finance: CEOs, CFOs, and other financial executives are prime targets for financial fraud, aiming for direct theft of funds or manipulation of financial transactions.
- Healthcare: Executives in healthcare are targeted to steal patient data, intellectual property related to research and development, or to disrupt operations.
- Technology: Technology companies are targeted for intellectual property theft, trade secrets, and sensitive customer data.
These industries and their executives represent lucrative targets for hackers due to the potential for significant financial gains and reputational damage. The attacks represent a significant [Specific Industry] cybersecurity breaches threat.
Financial Losses and the Impact of the Office365 Hacks
The financial impact of these Office365 breaches is staggering. Direct losses from financial fraud – including the theft of funds through unauthorized wire transfers – represent only a portion of the overall cost. Indirect costs such as remediation efforts, legal fees, reputational damage, and the cost of restoring data add significantly to the overall financial burden.
- Millions of dollars lost directly through wire transfer fraud and theft of funds.
- Significant costs associated with incident response, forensic investigations, and data recovery.
- Long-term reputational damage affecting customer trust and investor confidence.
These breaches can cripple organizations, leading to long-term consequences and impacting investor confidence. The costs extend far beyond the initial financial losses.
Preventing Future Office365 Executive Hacks: Best Practices and Security Measures
Organizations must proactively strengthen their Office365 security posture to mitigate the risk of similar attacks. A layered security approach is crucial, incorporating multiple layers of defense.
- Multi-factor authentication (MFA): Implementing MFA adds an extra layer of security, making it significantly harder for hackers to access accounts even if they obtain usernames and passwords.
- Security awareness training: Educating employees about phishing techniques and social engineering tactics is crucial in preventing them from falling victim to spear phishing attacks.
- Endpoint detection and response (EDR): EDR solutions can detect and respond to malicious activity on endpoints, preventing malware from executing and exfiltrating data.
- Regular software updates: Keeping all software, including Office365 applications, updated with the latest security patches is essential to mitigate known vulnerabilities.
- Strong passwords and password management: Enforcing strong, unique passwords and utilizing a password manager can significantly reduce the risk of credential stuffing attacks.
- Advanced threat protection: Utilizing advanced threat protection features within Office365 helps detect and block malicious emails and attachments before they reach users' inboxes.
Implementing these measures will contribute to a robust Office365 security framework and significantly reduce the risk of future breaches.
Conclusion: Safeguarding Your Organization from Office365 Executive Hacks
The federal investigation into these Office365 executive hacks has revealed a critical vulnerability and the immense financial losses resulting from successful attacks. The scale of the problem underscores the urgent need for proactive cybersecurity measures. To improve Office365 security, organizations must adopt a multi-layered approach, implementing the best practices outlined above. Failing to do so leaves your organization vulnerable to similar attacks, potentially resulting in significant financial losses and irreparable reputational damage. To prevent Office365 breaches, consider undertaking an Office365 security audit and seeking expert help to enhance cybersecurity and develop a comprehensive security strategy. Don't wait until it's too late; take action now to improve Office365 security and protect your organization.

Featured Posts
-
 Chalet Girls Unveiling The Reality Of Luxury Ski Resorts
Apr 23, 2025
Chalet Girls Unveiling The Reality Of Luxury Ski Resorts
Apr 23, 2025 -
 Radno Vrijeme Trgovina Za Uskrs I Uskrsni Ponedjeljak Vas Vodic
Apr 23, 2025
Radno Vrijeme Trgovina Za Uskrs I Uskrsni Ponedjeljak Vas Vodic
Apr 23, 2025 -
 Jackson Chourios Homer And 5 Rbis Fuel Brewers Win Against Rockies
Apr 23, 2025
Jackson Chourios Homer And 5 Rbis Fuel Brewers Win Against Rockies
Apr 23, 2025 -
 Rayadas Triunfa Con Doblete De Burky
Apr 23, 2025
Rayadas Triunfa Con Doblete De Burky
Apr 23, 2025 -
 Istanbul Da 3 Mart Pazartesi Guenue Iftar Ve Sahur Saatleri
Apr 23, 2025
Istanbul Da 3 Mart Pazartesi Guenue Iftar Ve Sahur Saatleri
Apr 23, 2025
Latest Posts
-
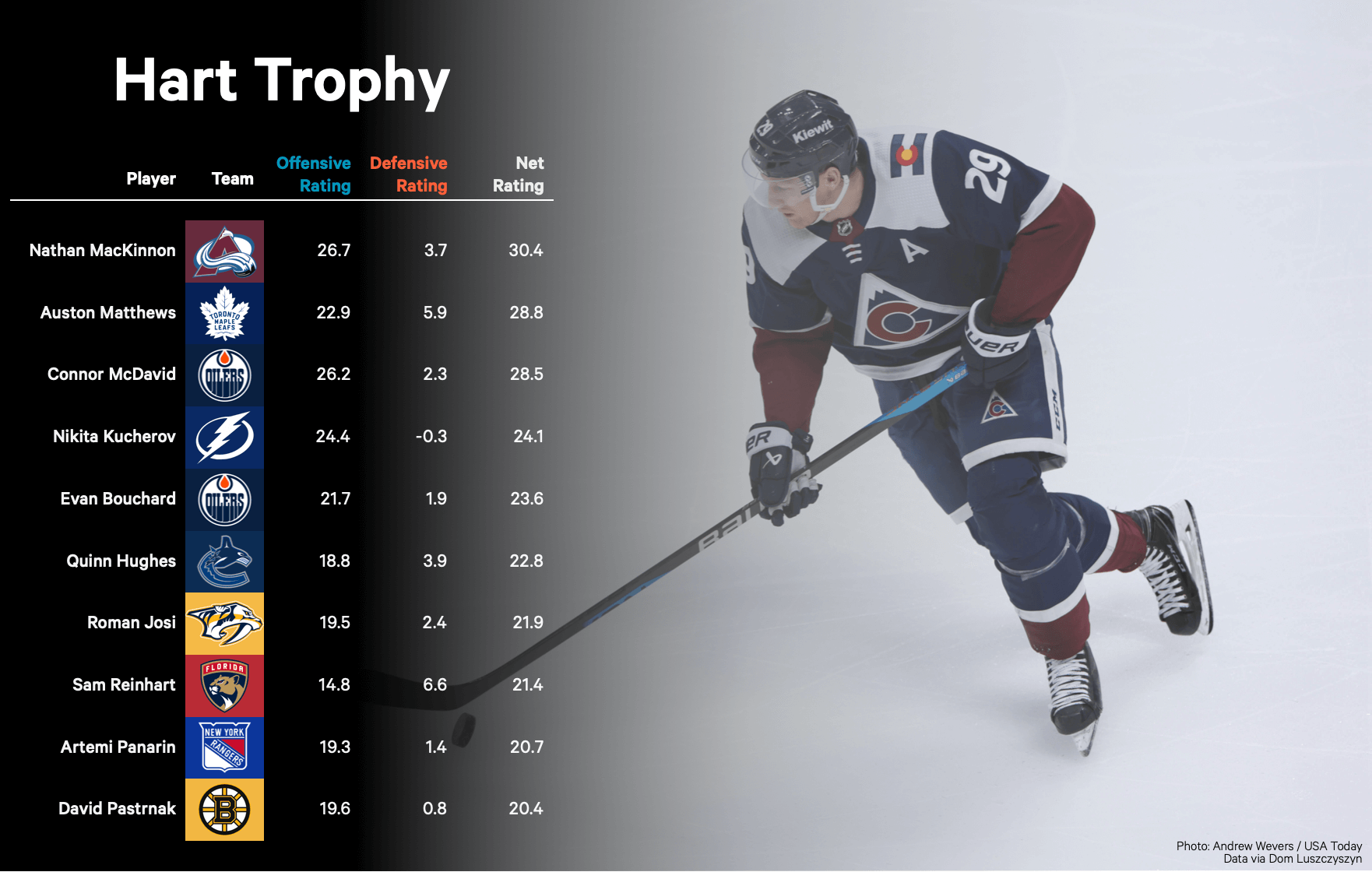 Three Stars Shine Draisaitl Hellebuyck And Kucherov In Hart Trophy Race
May 10, 2025
Three Stars Shine Draisaitl Hellebuyck And Kucherov In Hart Trophy Race
May 10, 2025 -
 Predicting The 2025 Nhl Playoffs After The Trade Deadline
May 10, 2025
Predicting The 2025 Nhl Playoffs After The Trade Deadline
May 10, 2025 -
 Draisaitl Hellebuyck And Kucherov 2023 Hart Trophy Finalists
May 10, 2025
Draisaitl Hellebuyck And Kucherov 2023 Hart Trophy Finalists
May 10, 2025 -
 2025 Nhl Trade Deadline Impact On Playoff Races
May 10, 2025
2025 Nhl Trade Deadline Impact On Playoff Races
May 10, 2025 -
 Nhl 2025 Trade Deadline Playoff Contender Predictions
May 10, 2025
Nhl 2025 Trade Deadline Playoff Contender Predictions
May 10, 2025
