Millions In Losses: Investigation Into Office365 Executive Hack

Table of Contents
The Modus Operandi: How the Office365 Executive Hack Was Executed
The attackers behind this particular Office365 executive hack utilized a multi-pronged approach combining advanced social engineering techniques with exploitation of known security weaknesses. This Office 365 security breach started with highly targeted phishing attacks.
- Spear Phishing and CEO Fraud: Attackers crafted convincing emails impersonating trusted individuals, including the CEO and other high-ranking executives. These emails contained malicious links or attachments designed to compromise the victim's accounts. This is a classic example of CEO fraud.
- Credential Stuffing and Multi-Factor Authentication Bypass: Once initial access was gained, attackers employed credential stuffing—attempting to log in using stolen credentials from other breaches—to gain access to further accounts. The lack of robust multi-factor authentication (MFA) allowed them to bypass security measures relatively easily.
- Malware Deployment: After gaining access, attackers deployed various types of malware, including ransomware to encrypt sensitive data and spyware to exfiltrate confidential information. This extended the initial Office 365 security breach into a far more damaging attack.
The Financial Fallout: Assessing the Millions in Losses from the Office365 Executive Hack
The financial repercussions of this Office365 executive hack were staggering. The direct costs included significant ransom payments, the expense of data recovery, and the cost of hiring cybersecurity experts to remediate the situation.
- Quantifiable Monetary Losses: While exact figures are often kept confidential due to legal and reputational reasons, estimates suggest losses exceeding several million dollars. This includes both direct and indirect costs.
- Cost of Recovery and Remediation: The process of restoring systems, recovering data, and enhancing security protocols involved significant expenditure, adding to the overall financial burden.
- Reputational Damage and Legal Fees: The breach caused substantial reputational damage, impacting investor confidence and potentially leading to significant legal fees and potential fines related to data privacy regulations. This is a significant cost often overlooked when calculating the total cost of an Office 365 data breach.
Security Gaps Exposed: Analyzing Vulnerabilities in Office365 Security
This incident exposed significant weaknesses in the organization's Office365 security posture. The attackers exploited several vulnerabilities, highlighting the critical need for comprehensive security measures.
- Weak Password Policies: The use of weak or easily guessable passwords facilitated initial account compromises. Strong, unique passwords for every account are essential.
- Lack of Multi-Factor Authentication (MFA): The absence of MFA was a critical vulnerability, allowing attackers to bypass security measures even after obtaining usernames and passwords. MFA should be mandated across all accounts.
- Insufficient Security Training: A lack of comprehensive security awareness training left employees vulnerable to sophisticated phishing attacks. Regular training is crucial to mitigate human error, a major factor in most security breaches. This Office365 security breach highlights the importance of employee training and awareness.
Lessons Learned: Best Practices to Prevent Future Office365 Executive Hacks
Preventing future Office365 executive hacks requires a multi-layered approach focused on proactive security measures and employee education.
- Implement Multi-Factor Authentication (MFA): MFA is crucial for adding an extra layer of security, significantly reducing the risk of unauthorized access.
- Enforce Strong Password Policies: Require complex, unique passwords and encourage the use of password managers.
- Conduct Regular Security Audits: Regular security assessments identify and address vulnerabilities before attackers can exploit them.
- Invest in Security Awareness Training: Train employees to recognize and report phishing attempts and other social engineering tactics.
- Utilize Advanced Threat Protection: Implement advanced threat protection tools to detect and respond to malicious activities in real-time.
Conclusion: Protecting Your Business from the Devastating Impact of an Office365 Executive Hack
This investigation into the devastating Office365 executive hack highlights the significant financial losses and security vulnerabilities that can be exploited. The lack of robust security measures, coupled with human error, created a perfect storm for attackers. To secure your Office365 environment and prevent an Office365 data breach, it's imperative to implement the best practices outlined above. Don't wait for a devastating attack to strike; strengthen your Office365 security today. Consider consulting with cybersecurity professionals to assess your current security posture and develop a comprehensive strategy to protect your organization from the crippling effects of an Office365 executive hack.

Featured Posts
-
 Post Roe America How Over The Counter Birth Control Changes The Game
Apr 23, 2025
Post Roe America How Over The Counter Birth Control Changes The Game
Apr 23, 2025 -
 Where To Invest A Map Of The Countrys Top Business Locations
Apr 23, 2025
Where To Invest A Map Of The Countrys Top Business Locations
Apr 23, 2025 -
 Guemueshane Okullar Tatil Mi 24 Subat Son Dakika Okul Durumu Ve Valilik Aciklamasi
Apr 23, 2025
Guemueshane Okullar Tatil Mi 24 Subat Son Dakika Okul Durumu Ve Valilik Aciklamasi
Apr 23, 2025 -
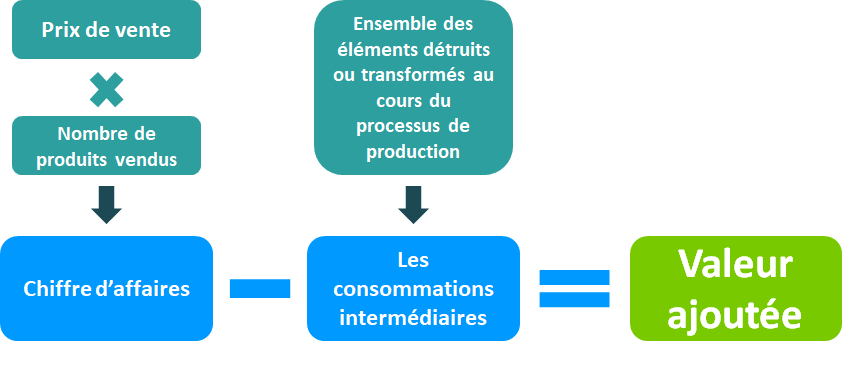 Infotel La Valeur Ajoutee Qui Fait La Difference
Apr 23, 2025
Infotel La Valeur Ajoutee Qui Fait La Difference
Apr 23, 2025 -
 Tensions Usa Russie L Augmentation Des Budgets De Defense Analysee Par John Plassard
Apr 23, 2025
Tensions Usa Russie L Augmentation Des Budgets De Defense Analysee Par John Plassard
Apr 23, 2025
Latest Posts
-
 Pam Bondis Plan To Kill American Citizens A Detailed Examination
May 10, 2025
Pam Bondis Plan To Kill American Citizens A Detailed Examination
May 10, 2025 -
 Elon Musks 300 Billion Net Worth Milestone Broken Analysis Of Recent Market Events
May 10, 2025
Elon Musks 300 Billion Net Worth Milestone Broken Analysis Of Recent Market Events
May 10, 2025 -
 Five Compelling Theories Unraveling Davids Identity In He Morgan Brothers High Potential
May 10, 2025
Five Compelling Theories Unraveling Davids Identity In He Morgan Brothers High Potential
May 10, 2025 -
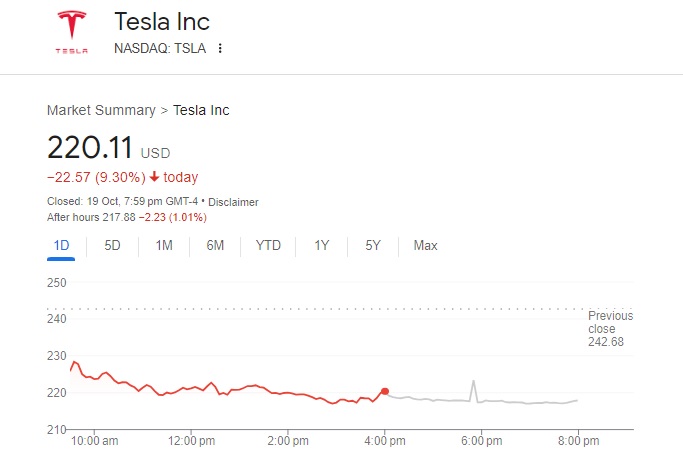 Tesla Stock Decline Impacts Elon Musks Net Worth Falling Below 300 Billion
May 10, 2025
Tesla Stock Decline Impacts Elon Musks Net Worth Falling Below 300 Billion
May 10, 2025 -
 Analyzing Abcs Decision Why Re Air High Potential Shows In March 2025
May 10, 2025
Analyzing Abcs Decision Why Re Air High Potential Shows In March 2025
May 10, 2025
