Millions Stolen After Hacker Targets Executive Office365 Accounts

Table of Contents
The Methodology of the Office365 Executive Account Breach
Cybercriminals employ increasingly sophisticated techniques to breach even the most secure systems. This Office365 security breach likely involved a combination of tactics:
-
Sophisticated Phishing Attacks: The attackers likely used highly targeted spear-phishing emails, meticulously crafted to mimic legitimate communications from trusted sources. These emails often contain malicious links or attachments designed to deliver malware or steal credentials. These spear-phishing campaigns often leverage information readily available online to personalize the attack and increase its effectiveness.
-
Credential Stuffing: Once initial access is gained, or attempted, attackers often utilize credential stuffing. This involves using lists of stolen usernames and passwords from previous data breaches to try and access accounts. This method relies on the reuse of passwords across multiple platforms, a common practice that significantly increases vulnerability.
-
Multi-Factor Authentication (MFA) Bypass: Bypassing MFA is a key challenge. Attackers may try to exploit vulnerabilities in MFA implementation or employ social engineering tactics to trick victims into revealing their authentication codes. This could involve manipulating legitimate MFA prompts or using compromised devices to intercept authentication codes.
-
Malware Deployment: Once inside the network, attackers often deploy malware to maintain persistent access and exfiltrate data. This malware can range from simple keyloggers to advanced tools capable of stealing sensitive information and controlling the compromised system. The malware might also be used to facilitate further attacks within the organization's network.
The Impact of the Executive Office365 Account Compromise
The consequences of an executive Office365 account compromise can be devastating:
-
Significant Financial Loss: In this case, millions of dollars were stolen through fraudulent wire transfers and other financial manipulations. This direct financial loss can cripple even large organizations.
-
Reputational Damage: Data breaches lead to significant reputational damage. Investor confidence erodes, customer loyalty declines, and the organization's overall brand image suffers. The resulting loss of trust can have long-term effects.
-
Regulatory Fines and Legal Ramifications: Non-compliance with data protection regulations, such as GDPR or CCPA, can result in substantial fines and legal battles. These costs can quickly escalate beyond the initial financial loss from the breach.
-
Data Theft Beyond Financial Information: The stolen data may include confidential business plans, intellectual property, customer data, and employee information – leading to further legal and financial ramifications.
Protecting Your Organization from Office365 Executive Account Attacks
Preventing these devastating Office365 security breaches demands a multi-faceted approach:
-
Robust Multi-Factor Authentication (MFA): Implement MFA for all Office365 accounts, especially executive accounts. This adds an extra layer of security, making it significantly harder for attackers to gain access even if they obtain credentials.
-
Comprehensive Security Awareness Training: Regular and thorough training is essential. Employees need to be educated on recognizing and avoiding phishing attempts, social engineering tactics, and other cyber threats. Simulations and regular testing are highly recommended.
-
Advanced Threat Protection Solutions: Invest in advanced solutions like Microsoft Defender for Office 365 and endpoint detection and response (EDR) systems. These tools provide proactive threat detection, malware prevention, and incident response capabilities.
-
Regular Security Policy Reviews: Security policies and procedures should be regularly reviewed and updated to reflect the latest threats and best practices. This includes password policies, access control measures, and incident response plans.
-
Threat Intelligence: Utilize threat intelligence feeds to stay informed about emerging threats and vulnerabilities. This proactive approach allows organizations to anticipate and mitigate risks before they can be exploited.
-
Strong Password Policies & Password Managers: Enforce strong password policies and encourage the use of password managers to improve password hygiene and reduce the risk of credential reuse.
The Role of Human Error in Office365 Security Breaches
Human error plays a significant role in many Office365 security breaches. Even the strongest technical security measures can be rendered ineffective by employee negligence:
-
Phishing Susceptibility: A single click on a malicious link in a phishing email can compromise an entire system. Employees need to be highly vigilant and trained to spot deceptive emails.
-
Social Engineering Vulnerabilities: Attackers often exploit human trust and urgency to gain access. Employees must be trained to question suspicious requests and verify the authenticity of communications.
-
Negligence: Seemingly small mistakes, such as reusing passwords or failing to report suspicious activity, can have catastrophic consequences.
Conclusion
The recent Office365 executive account breach, resulting in the theft of millions, serves as a stark reminder of the ever-evolving cybersecurity landscape. Protecting against such attacks requires a multi-layered approach combining robust technical security measures, comprehensive employee training, and a proactive security posture. Implementing strong multi-factor authentication, investing in advanced threat protection solutions, and fostering a culture of security awareness are crucial steps to prevent similar incidents. Don't wait for a devastating Office365 security breach to impact your organization – take decisive action today to safeguard your valuable assets and reputation. Strengthen your Office365 security now and protect your business from potential financial and reputational losses.

Featured Posts
-
 Top Universities Unite In Private Coalition Against Trump Administration
Apr 29, 2025
Top Universities Unite In Private Coalition Against Trump Administration
Apr 29, 2025 -
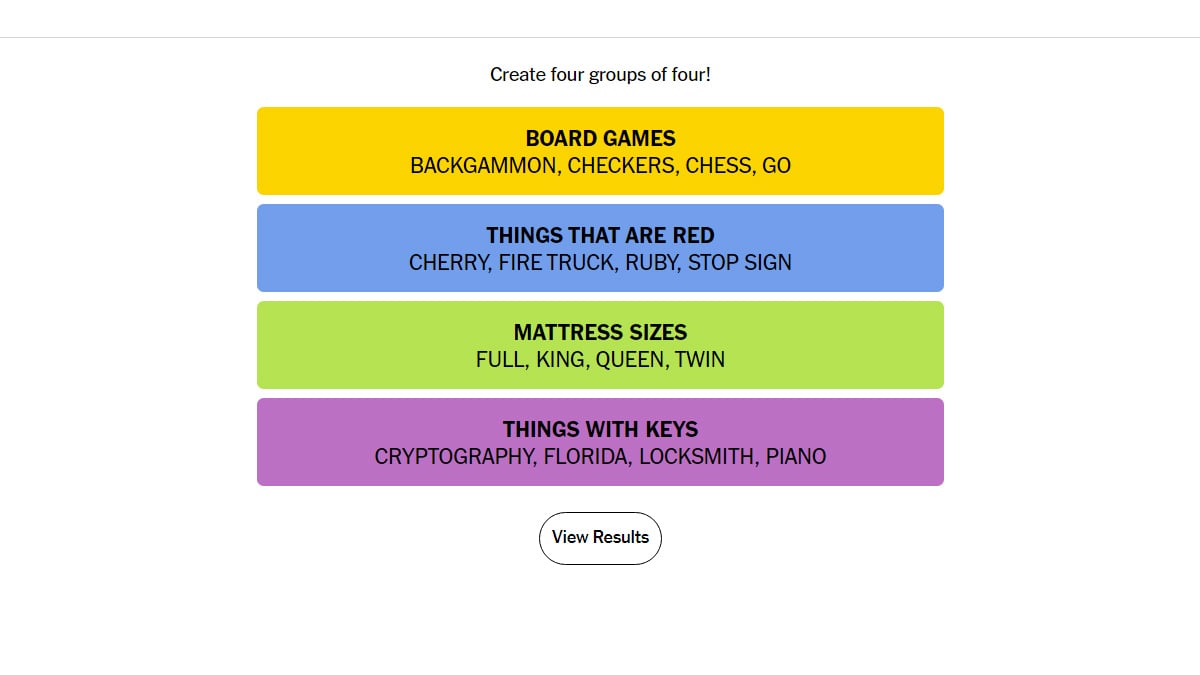 Solve Nyt Strands Hints And Answers For Puzzle On February 27 2025
Apr 29, 2025
Solve Nyt Strands Hints And Answers For Puzzle On February 27 2025
Apr 29, 2025 -
 Nyt Strands Game 422 Hints And Answers For April 29th Tuesday
Apr 29, 2025
Nyt Strands Game 422 Hints And Answers For April 29th Tuesday
Apr 29, 2025 -
 Unlock The Nyt Spelling Bee April 1 2025 Solutions And Answers
Apr 29, 2025
Unlock The Nyt Spelling Bee April 1 2025 Solutions And Answers
Apr 29, 2025 -
 Alberto Ardila Olivares Consistencia Y Garantia De Gol
Apr 29, 2025
Alberto Ardila Olivares Consistencia Y Garantia De Gol
Apr 29, 2025
Latest Posts
-
 Analyzing The Vmas Move To Cbs Implications For Mtv
May 12, 2025
Analyzing The Vmas Move To Cbs Implications For Mtv
May 12, 2025 -
 Ru Pauls Drag Race S17 E13 Drag Baby Mamas A Family Affair Preview
May 12, 2025
Ru Pauls Drag Race S17 E13 Drag Baby Mamas A Family Affair Preview
May 12, 2025 -
 The Cbs Vma Simulcast A Threat To Mtvs Dominance
May 12, 2025
The Cbs Vma Simulcast A Threat To Mtvs Dominance
May 12, 2025 -
 100 Mtv Unplugged Episodes Now Streaming The Complete List
May 12, 2025
100 Mtv Unplugged Episodes Now Streaming The Complete List
May 12, 2025 -
 Is Mtv Losing Its Grip Analyzing The Cbs Vma Simulcast Effect
May 12, 2025
Is Mtv Losing Its Grip Analyzing The Cbs Vma Simulcast Effect
May 12, 2025
