Millions Stolen: Inside The Office365 Breach Targeting Executive Inboxes

Table of Contents
The Sophistication of Office365 Phishing Attacks
Office365 phishing attacks are no longer simple attempts to trick users with generic emails. Modern attacks employ sophisticated techniques designed to bypass even the most robust security systems.
Advanced Persistent Threats (APTs)
Advanced Persistent Threats (APTs) represent a significant evolution in cybercrime, utilizing highly targeted and persistent attacks against specific organizations or individuals. These attacks go beyond simple phishing emails, often leveraging spear phishing, whaling, and business email compromise (BEC) tactics.
- Spear Phishing: Highly targeted emails that impersonate trusted individuals or organizations, often containing personalized information to increase their credibility.
- Whaling: A specific type of spear phishing that targets high-profile executives (the "big fish") within an organization.
- Business Email Compromise (BEC): Criminals compromise email accounts to send fraudulent requests for wire transfers or other financial transactions.
- Stolen Credentials: Attackers use stolen usernames and passwords to gain direct access to Office365 accounts.
- Compromised Email Accounts: Hackers infiltrate email accounts to monitor communications and steal sensitive information.
- Realistic Email Spoofing: Attackers create incredibly convincing emails that mimic legitimate communications from known senders, making it difficult to detect.
- A recent example involved a sophisticated APT campaign targeting a major financial institution, resulting in a multi-million dollar loss due to a compromised executive email account.
Exploiting Weaknesses in Multi-Factor Authentication (MFA)
Even with Multi-Factor Authentication (MFA) in place, attackers find ways to circumvent these security measures. They often target the human element, exploiting weaknesses in MFA implementations.
- Phishing for One-Time Codes: Attackers use sophisticated phishing techniques to trick users into revealing their one-time codes.
- Exploiting Vulnerabilities in MFA Implementations: Attackers may exploit vulnerabilities in the MFA software or system itself.
- Sim Swapping: Attackers illegally port the victim's phone number to a device they control, intercepting MFA codes sent via SMS.
Strong password management and robust MFA policies are crucial to mitigate these risks. Implementing a strong password policy, using a password manager, and enforcing multi-factor authentication with various methods (e.g., authenticator apps, security keys) are vital steps.
The Impact of Successful Office365 Breaches on Businesses
A successful Office365 breach can have devastating consequences for businesses, extending far beyond the immediate financial losses.
Financial Losses
The financial impact of an Office365 breach can be crippling. Costs include:
- Lost Funds: Direct financial losses from fraudulent transactions and wire transfers.
- Legal Fees: Expenses associated with legal investigations and potential lawsuits.
- Remediation Costs: The cost of investigating the breach, recovering data, and implementing enhanced security measures.
- Reputational Damage: Loss of customer trust and damage to brand reputation can lead to decreased revenue.
Reputational Damage and Loss of Customer Trust
A data breach severely damages a company's reputation and erodes customer trust.
- Negative Publicity: News reports and social media discussions can negatively impact public perception.
- Loss of Customers: Customers may switch to competitors due to concerns about data security.
- Difficulty Attracting Investors: A damaged reputation can make it harder to secure funding.
Legal and Regulatory Compliance Issues
Breaches can result in significant legal repercussions and regulatory non-compliance.
- GDPR Fines: Non-compliance with the General Data Protection Regulation (GDPR) can result in substantial fines.
- CCPA Penalties: Failure to adhere to the California Consumer Privacy Act (CCPA) can also lead to penalties.
- Lawsuits: Businesses may face lawsuits from affected individuals and regulatory bodies.
Protecting Your Organization from Office365 Breaches
Protecting your organization requires a multi-layered approach focusing on enhanced security measures and employee awareness.
Strengthening Email Security
Improving email security is paramount in preventing Office365 breaches.
- SPF, DKIM, DMARC: Implement these email authentication protocols to verify the sender's authenticity.
- Advanced Threat Protection: Utilize advanced threat protection solutions to identify and block malicious emails.
- Anti-phishing Training: Regular training for employees to identify and report phishing attempts.
Implementing Robust MFA and Access Controls
Strong authentication and access controls are critical:
- Strong Passwords: Enforce complex and unique passwords for all accounts.
- Multi-Factor Authentication (MFA): Implement strong MFA across all Office365 accounts.
- Least Privilege Access: Grant users only the necessary access privileges to perform their jobs.
Employee Security Awareness Training
Regular security awareness training is crucial:
- Phishing Simulations: Conduct regular phishing simulations to assess employee awareness.
- Security Awareness Campaigns: Develop and implement ongoing security awareness campaigns.
- Reporting Procedures: Establish clear procedures for reporting suspicious emails and activities.
Regular Security Audits and Penetration Testing
Regular assessments identify vulnerabilities:
- Vulnerability Scanning: Regularly scan for vulnerabilities in your systems.
- Penetration Testing: Simulate real-world attacks to identify weaknesses in your security posture.
- Security Information and Event Management (SIEM): Implement a SIEM system to monitor security logs and detect suspicious activity.
Conclusion
Office365 breaches targeting executives are sophisticated attacks with devastating consequences. The financial losses, reputational damage, and legal repercussions can be crippling. Proactive measures, including robust email security, strong MFA, employee training, and regular security audits, are essential to protect your organization. Don't become another statistic. Invest in robust Office365 security solutions and employee training to prevent devastating Office365 breaches and safeguard your business from financial and reputational damage. Explore advanced threat protection solutions and security awareness training programs today to strengthen your defenses.

Featured Posts
-
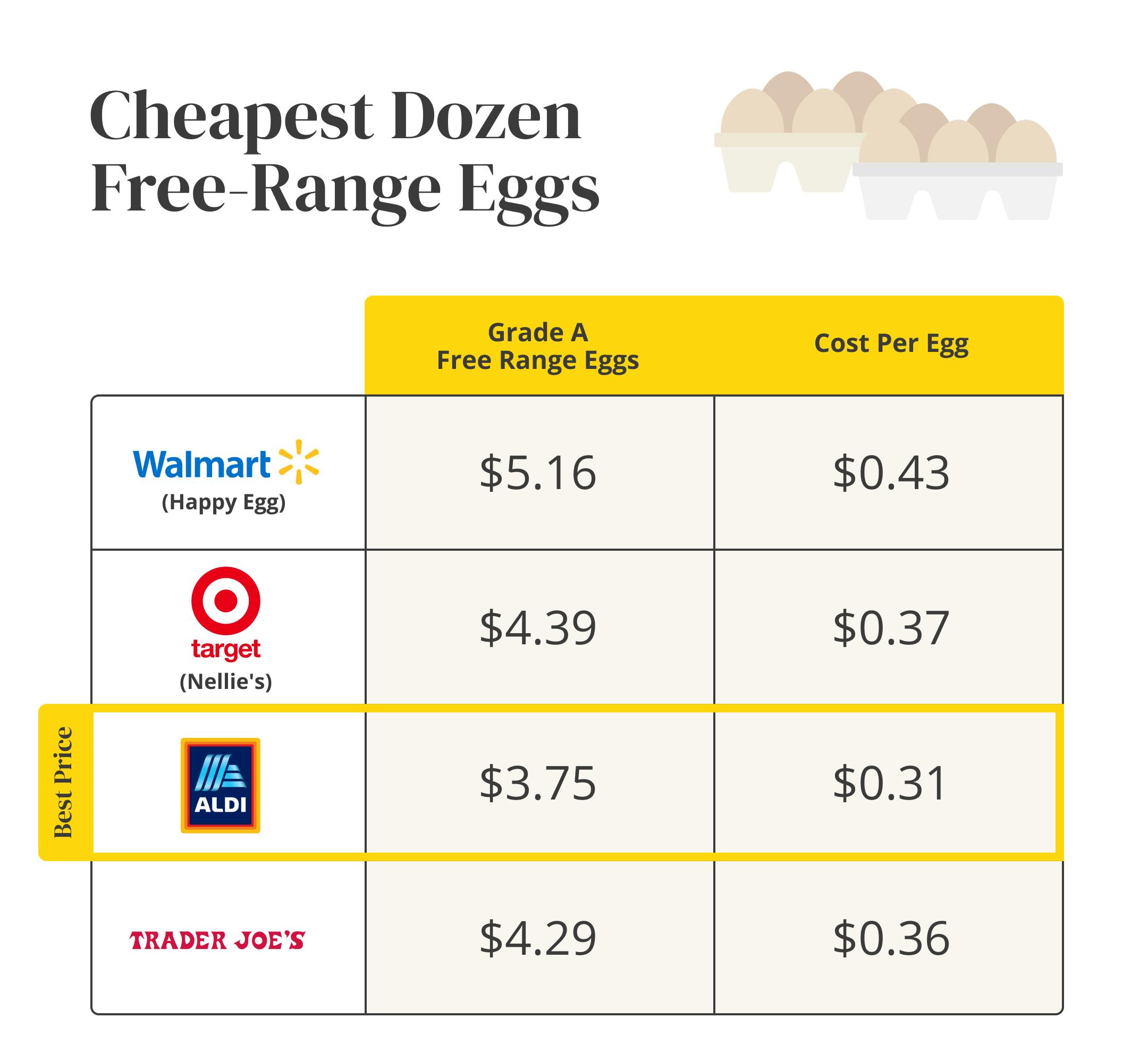 Lower Egg Prices Us Consumers Now Pay 5 Per Dozen
May 16, 2025
Lower Egg Prices Us Consumers Now Pay 5 Per Dozen
May 16, 2025 -
 Ayesha Howard Awarded Custody After Paternity Dispute With Anthony Edwards
May 16, 2025
Ayesha Howard Awarded Custody After Paternity Dispute With Anthony Edwards
May 16, 2025 -
 How Ha Seong Kim And Blake Snells Friendship Benefits Korean Mlb Players
May 16, 2025
How Ha Seong Kim And Blake Snells Friendship Benefits Korean Mlb Players
May 16, 2025 -
 Chicago Cubs Poteet Conquers Spring Training Abs Challenge
May 16, 2025
Chicago Cubs Poteet Conquers Spring Training Abs Challenge
May 16, 2025 -
 Dodgers Left Handed Hitters Overcoming The Slump And Returning To Form
May 16, 2025
Dodgers Left Handed Hitters Overcoming The Slump And Returning To Form
May 16, 2025
Latest Posts
-
 Colorado Rapids Defeat Opponent Calvin Harris Cole Bassett Goals Steffens Strong Performance
May 16, 2025
Colorado Rapids Defeat Opponent Calvin Harris Cole Bassett Goals Steffens Strong Performance
May 16, 2025 -
 Lafc Prioritizes Mls San Jose Game A Key Indicator
May 16, 2025
Lafc Prioritizes Mls San Jose Game A Key Indicator
May 16, 2025 -
 Shorthanded Timbers Fall To San Jose Ending Seven Match Unbeaten Run
May 16, 2025
Shorthanded Timbers Fall To San Jose Ending Seven Match Unbeaten Run
May 16, 2025 -
 San Jose Vs Lafc Mls Match Highlights Lafcs Shift In Priorities
May 16, 2025
San Jose Vs Lafc Mls Match Highlights Lafcs Shift In Priorities
May 16, 2025 -
 Portland Timbers Unbeaten Streak Ends At Seven Games Against San Jose
May 16, 2025
Portland Timbers Unbeaten Streak Ends At Seven Games Against San Jose
May 16, 2025
