Office365 Executive Inboxes Targeted: Millions Lost In Cybercrime

Table of Contents
The Sophistication of Modern Office365 Phishing Attacks
Modern phishing attacks targeting Office365 executive inboxes are far more sophisticated than their predecessors. Attackers employ advanced techniques to bypass security measures and gain access to sensitive data.
Impersonation Techniques
Attackers go to great lengths to impersonate CEOs, CFOs, and other high-ranking officials to lend credibility to their malicious communications. This often involves:
- Spoofed email addresses: Attackers create email addresses that closely resemble legitimate ones, differing only by a single character or using similar domain names.
- Realistic email signatures: They meticulously craft email signatures that mirror those of their targets, including titles, contact information, and even logos.
- Urgency tactics: Creating a sense of urgency, such as demanding immediate action on a supposedly critical matter, pressures recipients into making hasty decisions without verifying the request.
- Exploiting known relationships: Attackers research their targets to understand their professional network and use this knowledge to craft highly personalized and convincing phishing emails, often referencing projects or individuals the executive knows.
This level of personalization significantly increases the success rate of these attacks, as recipients are less likely to detect the deception.
Advanced Persistent Threats (APTs)
Advanced Persistent Threats (APTs) represent a particularly insidious form of attack. These are long-term, targeted cyberattacks designed to maintain persistent access to a victim's systems. APTs often involve:
- Data exfiltration: Stealing sensitive data such as financial records, intellectual property, and customer information over an extended period.
- Malware deployment: Installing malware to monitor activity, control systems, and facilitate further attacks.
- Persistent access: Maintaining unauthorized access to the victim's systems for months or even years.
- Compromised credentials: Stealing login credentials to gain access to other accounts and systems.
Detecting and mitigating APTs requires advanced security solutions and a proactive security posture.
Common Tactics Used in Office365 Executive Inbox Attacks
Several common tactics are employed in Office365 executive inbox attacks. Understanding these tactics is crucial for developing effective preventative measures.
Spear Phishing
Spear phishing attacks are highly targeted campaigns specifically aimed at executives. These attacks leverage:
- Highly personalized emails: Emails tailored to the individual executive, referencing specific projects, colleagues, or company information.
- Attachment-based attacks: Malicious attachments disguised as legitimate documents, such as invoices or contracts, designed to deliver malware.
- URL-based attacks: Links embedded in emails that redirect to malicious websites designed to steal credentials or install malware.
- Social engineering: Manipulating the recipient's psychology to trick them into taking actions that compromise their security.
These attacks are designed to bypass spam filters and security software by appearing legitimate and relevant to the recipient.
Business Email Compromise (BEC)
Business Email Compromise (BEC) attacks focus on financially motivated fraud. Attackers impersonate executives or vendors to manipulate financial transactions, including:
- Wire transfer fraud: Directing funds to fraudulent accounts.
- Invoice scams: Submitting fraudulent invoices for payment.
- Payroll manipulation: Diverting payroll funds to attacker-controlled accounts.
- Vendor impersonation: Requesting payments to fraudulent vendor accounts.
BEC attacks often result in significant financial losses for businesses. For example, a recent BEC attack cost a company millions by impersonating the CEO and requesting a large wire transfer.
Protecting Your Office365 Executive Inboxes
Protecting your Office365 executive inboxes requires a multi-layered approach that combines technical solutions with employee training and awareness.
Implementing Robust Security Measures
Businesses must implement robust security measures to mitigate the risks associated with Office365 executive inbox attacks. These include:
- Multi-factor authentication (MFA): Adding an extra layer of security to account logins, significantly reducing the risk of unauthorized access.
- Strong password policies: Enforcing the use of strong, unique passwords for all accounts.
- Email security solutions: Implementing advanced email security solutions to detect and block phishing emails and malicious attachments.
- Employee training: Educating employees about phishing scams and other cyber threats.
- Regular security audits: Conducting regular security audits to identify vulnerabilities and ensure the effectiveness of security measures.
Leveraging Advanced Threat Protection (ATP)
Microsoft's Advanced Threat Protection (ATP) and similar solutions offer advanced capabilities to detect and prevent sophisticated attacks. These include:
- Anti-phishing features: Detecting and blocking phishing emails based on advanced analysis techniques.
- Anti-malware protection: Scanning emails and attachments for malware.
- Sandboxing: Safely analyzing suspicious attachments and links in a controlled environment.
- URL analysis: Checking URLs for malicious activity before users click them.
- Real-time threat intelligence: Leveraging real-time threat intelligence to identify and block emerging threats.
Conclusion
The threat of Office365 executive inbox compromises is real and significant, resulting in millions of dollars in financial losses for businesses worldwide. The sophistication of these attacks necessitates a proactive and multi-faceted approach to security. By implementing robust security measures, such as multi-factor authentication, strong password policies, advanced email security solutions, and employee training, businesses can significantly reduce their risk. Investing in solutions like Microsoft's Advanced Threat Protection (ATP) is crucial for detecting and preventing the most sophisticated attacks. Don't become another statistic. Protect your Office365 executive inboxes today by implementing strong security measures and investing in advanced threat protection. Learn more about securing your Microsoft 365 environment and preventing costly Office365 executive inbox attacks.

Featured Posts
-
 Retired Four Star Admiral Convicted Corruption Scandal Details
May 21, 2025
Retired Four Star Admiral Convicted Corruption Scandal Details
May 21, 2025 -
 Juergen Klopp Un Doenuesue Duenya Devi Nin Yeni Teknik Direktoerue
May 21, 2025
Juergen Klopp Un Doenuesue Duenya Devi Nin Yeni Teknik Direktoerue
May 21, 2025 -
 Bwtshytynw Ystdey Thlathy Jdyd Lmntkhb Amryka
May 21, 2025
Bwtshytynw Ystdey Thlathy Jdyd Lmntkhb Amryka
May 21, 2025 -
 Blue Origin Postpones Launch Investigating Vehicle Issue
May 21, 2025
Blue Origin Postpones Launch Investigating Vehicle Issue
May 21, 2025 -
 Me Bwtshytynw Thlatht Wjwh Jdydt Fy Mntkhb Amryka
May 21, 2025
Me Bwtshytynw Thlatht Wjwh Jdydt Fy Mntkhb Amryka
May 21, 2025
Latest Posts
-
 Mild Temperatures And Little Rain Chance A Perfect Week Ahead
May 21, 2025
Mild Temperatures And Little Rain Chance A Perfect Week Ahead
May 21, 2025 -
 Scott Savilles Dedication Years Of Cycling Ragbrai And Daily Rides
May 21, 2025
Scott Savilles Dedication Years Of Cycling Ragbrai And Daily Rides
May 21, 2025 -
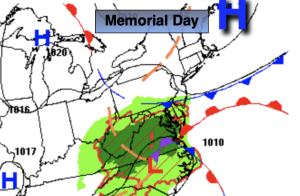 Understanding Breezy And Mild Weather Patterns A Practical Overview
May 21, 2025
Understanding Breezy And Mild Weather Patterns A Practical Overview
May 21, 2025 -
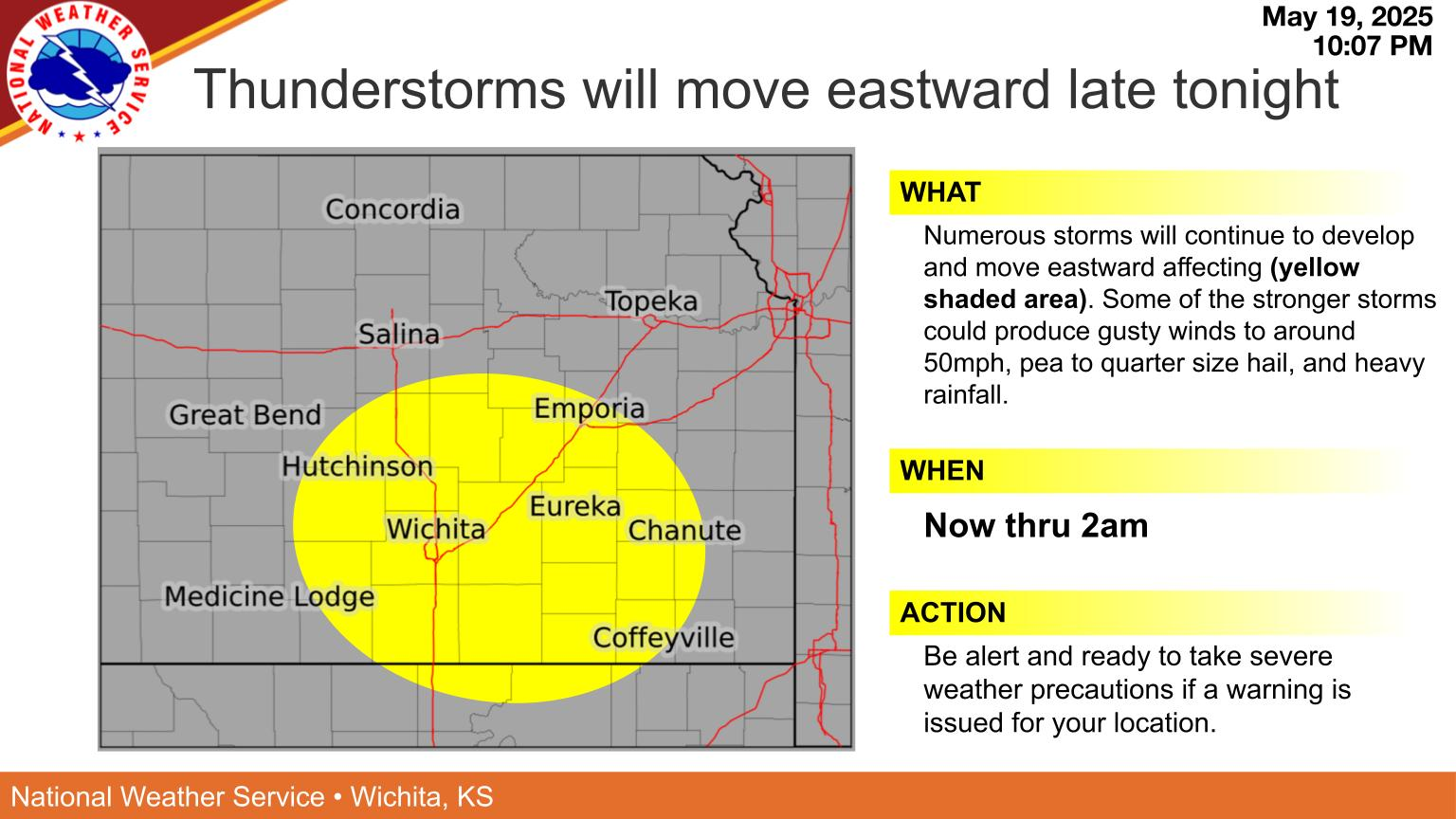 Planning Your Week Expect Mild Temperatures And Little Rain Chance
May 21, 2025
Planning Your Week Expect Mild Temperatures And Little Rain Chance
May 21, 2025 -
 Breezy And Mild Destinations Where To Find The Perfect Climate
May 21, 2025
Breezy And Mild Destinations Where To Find The Perfect Climate
May 21, 2025
