Office365 Security Breach: Millions In Losses Reported
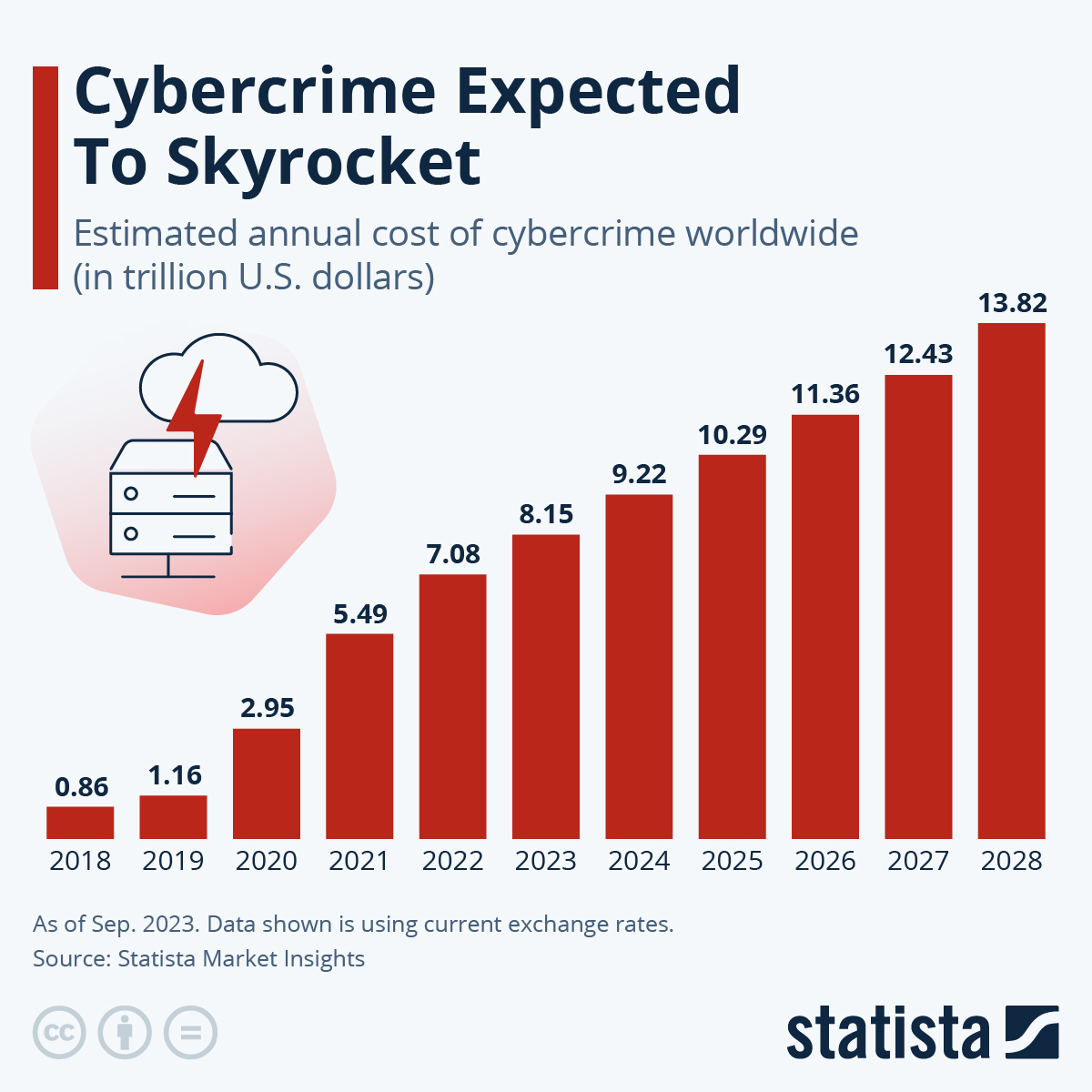
Table of Contents
The Rising Threat of Office365 Breaches
The seemingly secure environment of Office365 is not immune to sophisticated cyberattacks. The rise in Office365 security breaches is fueled by increasingly sophisticated attack methods and a lack of awareness among users.
Common Attack Vectors
Cybercriminals employ various methods to breach Office365 security. These include:
- Phishing emails targeting user credentials: Deceptive emails mimicking legitimate communications trick users into revealing their login details, granting attackers direct access to their accounts and potentially the entire organizational network. These often include malicious attachments or links leading to phishing websites.
- Exploiting vulnerabilities in outdated software and plugins: Failing to update software leaves systems vulnerable to known exploits. Outdated plugins, especially those not regularly updated by their developers, represent significant security risks.
- Malware infections gaining access to sensitive data: Malware can be introduced through infected attachments, malicious links, or compromised websites, providing attackers with a backdoor into the Office365 environment to steal data or deploy ransomware.
- Brute-force attacks targeting weak passwords: Attackers use automated tools to try numerous password combinations until they gain access. Weak or easily guessable passwords are particularly vulnerable.
- Compromised third-party applications with access to Office365 data: Applications granted access to Office365 data, if insecure, can provide an entry point for attackers. Careful vetting and ongoing monitoring of third-party integrations are essential.
Types of Data Breaches
The consequences of a successful Office365 security breach can be devastating, encompassing several types of data loss:
- Data exfiltration: Attackers steal sensitive customer data, intellectual property, financial records, and other confidential information, potentially leading to significant financial losses and reputational damage.
- Ransomware attacks: Crucial files are encrypted, rendering them inaccessible unless a ransom is paid. This can cripple business operations and lead to significant downtime and recovery costs.
- Account takeover: Attackers gain unauthorized access to organizational accounts, modifying data, sending fraudulent emails, and disrupting communications.
- Business email compromise (BEC): Attackers impersonate executives to initiate fraudulent financial transactions, leading to substantial monetary losses.
- Data leaks due to misconfigurations or lack of access controls: Improperly configured settings or inadequate access controls can inadvertently expose sensitive data, creating vulnerabilities that attackers can exploit.
Minimizing Your Risk: Best Practices for Office365 Security
Protecting your organization from Office365 security breaches requires a multi-layered approach encompassing various security best practices.
Implement Strong Password Policies and Multi-Factor Authentication (MFA)
- Enforce complex password requirements: Mandate strong passwords with a mix of uppercase and lowercase letters, numbers, and symbols.
- Mandatory MFA for all users: Utilize a variety of authentication methods, including one-time passwords, biometric authentication, and security keys. This adds an extra layer of security, even if passwords are compromised.
- Regular password rotation and security awareness training for employees: Educate employees on the importance of strong password hygiene and the dangers of phishing attacks.
Regular Software Updates and Patching
- Keep all Office365 applications, plugins, and operating systems updated: Apply security patches promptly to address known vulnerabilities.
- Implement automated patching systems: Automate the update process to minimize the risk of human error and ensure timely patching.
Advanced Threat Protection (ATP) and Security Information and Event Management (SIEM)
- Leverage Office365 ATP features: Detect and prevent malicious emails and files before they reach users' inboxes.
- Utilize SIEM tools: Monitor and analyze security logs for suspicious activity, providing early warning of potential breaches.
Employee Security Awareness Training
- Regularly educate employees: Train them on identifying and avoiding phishing attacks, malware, and social engineering techniques. Phishing simulations are invaluable.
- Conduct simulated phishing campaigns: Test employee awareness and reinforce training by sending simulated phishing emails.
Data Loss Prevention (DLP) Measures
- Implement DLP policies: Prevent sensitive data from leaving the organization's network.
- Monitor data access and usage patterns: Identify potential leaks and unauthorized access attempts.
The Cost of an Office365 Security Breach
The financial impact of an Office365 security breach extends far beyond the immediate costs.
Direct Financial Losses
- Ransom payments: Paying ransoms to regain access to encrypted data.
- Legal and regulatory fines: Penalties for failing to comply with data protection regulations.
- Cost of incident response and data recovery: Expenses associated with investigating the breach, restoring data, and notifying affected parties.
Indirect Costs
- Reputational damage and loss of customer trust: Damage to brand reputation impacting future business.
- Disruption to business operations and productivity: Downtime caused by the breach disrupting workflow.
- Loss of intellectual property and competitive advantage: Compromised intellectual property can significantly impact a business's competitive standing.
Conclusion
The threat of an Office365 security breach is real and the consequences can be financially and reputationally devastating. From phishing attacks to ransomware and data exfiltration, the potential attack vectors are numerous. Implementing robust security measures, including multi-factor authentication (MFA), regular software updates, comprehensive employee training, and advanced threat protection (ATP), is paramount. Proactive security management is not merely a cost; it's an investment in protecting your business's valuable data and future. Protect your business from the devastating impact of an Office365 security breach. Implement comprehensive security protocols today and safeguard your valuable data.

Featured Posts
-
 Brewers 9 Cubs 7 Windy City Wallop
Apr 23, 2025
Brewers 9 Cubs 7 Windy City Wallop
Apr 23, 2025 -
 Solutions 30 Hausse Boursiere Perspectives Et Objectifs D Investissement
Apr 23, 2025
Solutions 30 Hausse Boursiere Perspectives Et Objectifs D Investissement
Apr 23, 2025 -
 China Seeks Canadian Oil As Us Trade War Intensifies
Apr 23, 2025
China Seeks Canadian Oil As Us Trade War Intensifies
Apr 23, 2025 -
 Istanbul Da Pazartesi Okullar Tatil Mi
Apr 23, 2025
Istanbul Da Pazartesi Okullar Tatil Mi
Apr 23, 2025 -
 5 2 Win For Diamondbacks Key Moments From The Brewers Game
Apr 23, 2025
5 2 Win For Diamondbacks Key Moments From The Brewers Game
Apr 23, 2025
Latest Posts
-
 How To Watch And Enjoy Celebrity Antiques Road Trip
May 10, 2025
How To Watch And Enjoy Celebrity Antiques Road Trip
May 10, 2025 -
 Exploring The Themes Of Wynne And Joanna All At Sea
May 10, 2025
Exploring The Themes Of Wynne And Joanna All At Sea
May 10, 2025 -
 Wynne Evans Dropped From Go Compare Ads After Sexism Scandal
May 10, 2025
Wynne Evans Dropped From Go Compare Ads After Sexism Scandal
May 10, 2025 -
 Celebrity Antiques Road Trip Top Moments And Memorable Finds
May 10, 2025
Celebrity Antiques Road Trip Top Moments And Memorable Finds
May 10, 2025 -
 Exploring The World Of Celebrity Antiques Road Trip A Comprehensive Overview
May 10, 2025
Exploring The World Of Celebrity Antiques Road Trip A Comprehensive Overview
May 10, 2025
