Corporate Email Compromise: Crook Makes Millions From Office365 Breaches
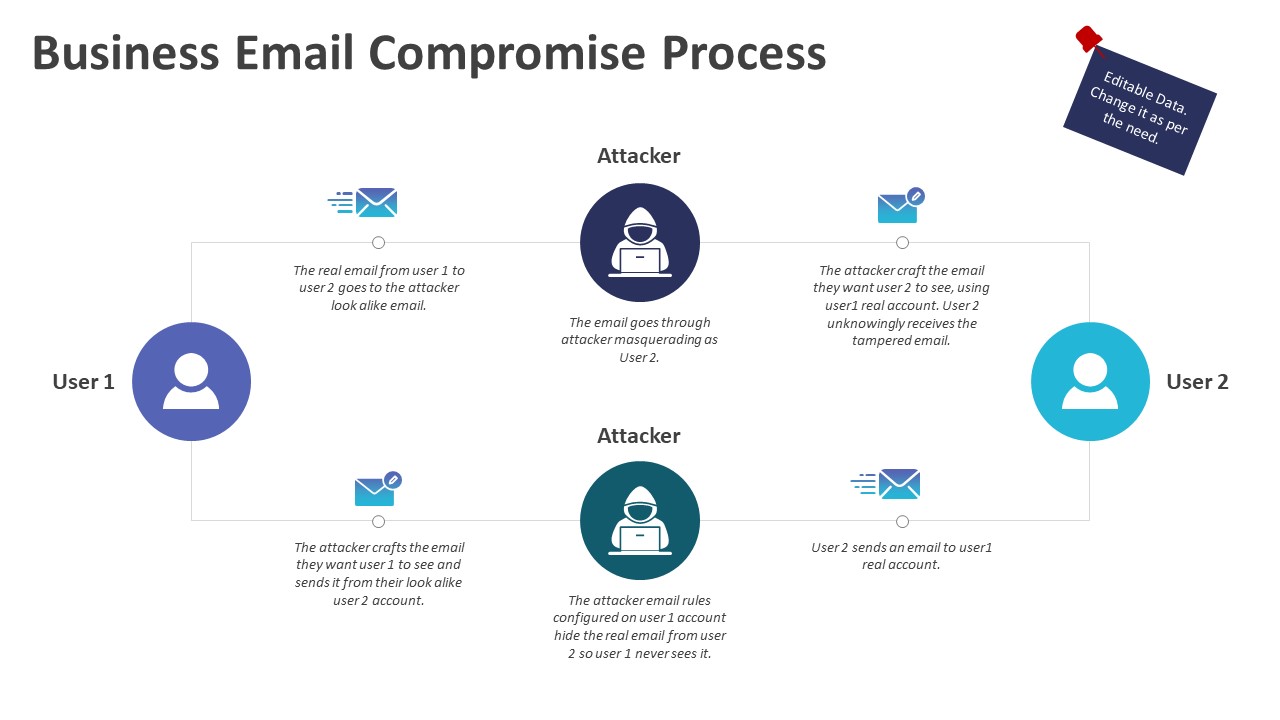
Table of Contents
Understanding Corporate Email Compromise (CEC) and its Tactics
Corporate Email Compromise leverages various tactics to infiltrate your Office365 environment and gain access to sensitive data. Let's explore the most prevalent methods:
Phishing and Spear Phishing Attacks
Phishing attacks rely on deceptive emails to trick users into revealing sensitive information or downloading malware. Spear phishing is a more targeted approach, personalizing emails to appear legitimate and increase the chances of success.
- Mechanics: Phishing emails often contain malicious links that redirect to fake login pages or attachments that install malware. Spear phishing emails might impersonate executives, vendors, or clients, using familiar names and communication styles to build trust.
- Tactics: Examples include emails demanding urgent payments, requests for sensitive data, or notifications about seemingly critical system issues. These often include convincing but fraudulent details.
- Examples: A convincing email mimicking your CEO requesting a wire transfer, or an invoice attachment containing a macro virus.
- Social Engineering: Hackers use social engineering techniques to manipulate employees' emotions, creating a sense of urgency or fear to compel quick actions without verification.
Credential Stuffing and Brute-Force Attacks
Hackers also attempt to gain access to Office365 accounts by trying various password combinations.
- Credential Stuffing: This involves using lists of stolen usernames and passwords obtained from data breaches on other platforms. These lists are then tested against Office365 accounts.
- Brute-Force Attacks: Hackers use automated tools to try countless password combinations until they find the correct one.
- Password Security: Strong, unique passwords are crucial to prevent these attacks. Avoid easily guessable passwords and use a password manager to generate and securely store complex credentials.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security, requiring a second verification method (like a code from your phone) in addition to your password. This significantly reduces the effectiveness of credential stuffing and brute-force attacks.
Exploiting Vulbilities in Office365
Office365, while generally secure, can still be vulnerable to exploitation if not properly configured and maintained.
- Security Settings: Weak security settings, such as default configurations or improperly configured access controls, create potential entry points for attackers.
- Outdated Software: Running outdated software leaves your system susceptible to known vulnerabilities. Regular updates and patches are essential to protect against exploits.
- Session Hijacking: Attackers might attempt to steal your active session cookies to gain unauthorized access to your Office365 account.
- Man-in-the-Middle (MitM) Attacks: These attacks intercept communication between your computer and Office365, allowing the attacker to steal data or inject malware.
The Devastating Impact of Office365 Breaches
The consequences of a successful Office365 breach can be far-reaching and devastating.
Financial Losses
CEC attacks can result in substantial financial losses.
- Quantifiable Damage: Millions of dollars can be lost through fraudulent wire transfers, invoice scams, and theft of intellectual property.
- Statistics: Reports show average losses ranging from thousands to millions depending on the size and nature of the business.
- Reputational Impact: The resulting damage to company reputation and shareholder value can be significant and long-lasting.
Reputational Damage
A data breach severely impacts a company's reputation and trust.
- Erosion of Customer Trust: Customers may lose confidence in your ability to protect their data, leading to decreased sales and market share.
- Negative Media Coverage: News of a data breach can damage your brand image and lead to negative publicity.
- Long-Term Impact: The effects on brand loyalty and customer relationships can persist for years.
Legal and Regulatory Penalties
Breaches can result in significant legal and regulatory consequences.
- Fines and Lawsuits: Businesses face potential fines and lawsuits from affected customers and regulatory bodies.
- Compliance Issues: Non-compliance with regulations like GDPR and CCPA can result in substantial penalties.
- Data Breach Notification Laws: Many jurisdictions mandate notification of affected individuals and authorities following a data breach.
Protecting Your Business from Office365 Corporate Email Compromise
Proactive measures are vital to protect your organization from CEC attacks.
Implementing Robust Security Measures
A multi-layered approach is crucial for robust email security.
- Multi-Factor Authentication (MFA): Mandatory MFA is a non-negotiable security best practice.
- Security Awareness Training: Regularly train employees to recognize and avoid phishing attempts.
- Strong Password Policies: Enforce strong password policies and encourage the use of password managers.
- Advanced Threat Protection: Implement advanced threat protection solutions to detect and block malicious emails and attachments.
Utilizing Advanced Security Tools
Leverage advanced tools to enhance your email security posture.
- Advanced Threat Protection: This includes features like sandboxing, anti-malware, and anti-phishing capabilities.
- Email Authentication Protocols (DMARC, SPF, DKIM): These protocols help verify the sender's identity and prevent email spoofing.
- Data Loss Prevention (DLP): DLP tools help prevent sensitive data from leaving your organization's network.
- Security Audits and Penetration Testing: Regularly conduct security audits and penetration testing to identify vulnerabilities.
Developing an Incident Response Plan
Having a well-defined incident response plan is critical in the event of a breach.
- Documented Plan: Create a comprehensive plan outlining steps to take if a breach occurs.
- Rapid Detection and Containment: Quick action is essential to minimize damage.
- Cybersecurity Experts: Involve cybersecurity experts to help investigate and remediate the breach.
Conclusion
Corporate Email Compromise (CEC) targeting Office365 poses a significant threat to businesses of all sizes. Understanding the methods used, the potential consequences, and implementing robust security measures are critical for minimizing risk. The impact of Business Email Compromise (BEC) on email security cannot be understated. Don't become another victim of an Office365 corporate email compromise. Invest in comprehensive email security solutions and employee training to safeguard your business from financial losses and reputational damage. Proactively protect your organization from the devastating impact of a Corporate Email Compromise and secure your valuable data.

Featured Posts
-
 Amundi Djia Ucits Etf Dist Factors Affecting Net Asset Value
May 24, 2025
Amundi Djia Ucits Etf Dist Factors Affecting Net Asset Value
May 24, 2025 -
 Rekomendasi Dayamitra Telekomunikasi Mtel And Merdeka Battery Mbma Pasca Masuk Msci Small Cap Index
May 24, 2025
Rekomendasi Dayamitra Telekomunikasi Mtel And Merdeka Battery Mbma Pasca Masuk Msci Small Cap Index
May 24, 2025 -
 Ronan Farrows Role In Mia Farrows Potential Comeback
May 24, 2025
Ronan Farrows Role In Mia Farrows Potential Comeback
May 24, 2025 -
 Jonathan Groff And Asexuality A Candid Conversation
May 24, 2025
Jonathan Groff And Asexuality A Candid Conversation
May 24, 2025 -
 Are Thames Water Executive Bonuses Justified A Critical Analysis
May 24, 2025
Are Thames Water Executive Bonuses Justified A Critical Analysis
May 24, 2025
Latest Posts
-
 Bestechung An Der Uni Duisburg Essen Umfang Des Skandals Und Gestaendnis Einer Mitarbeiterin
May 24, 2025
Bestechung An Der Uni Duisburg Essen Umfang Des Skandals Und Gestaendnis Einer Mitarbeiterin
May 24, 2025 -
 Radtouren Durch Essen Persoenlichkeiten Entdecken Und Die Seele Baumeln Lassen
May 24, 2025
Radtouren Durch Essen Persoenlichkeiten Entdecken Und Die Seele Baumeln Lassen
May 24, 2025 -
 Complete Guide To Solving The Nyt Mini Crossword April 8 2025
May 24, 2025
Complete Guide To Solving The Nyt Mini Crossword April 8 2025
May 24, 2025 -
 Nyt Mini Crossword Puzzle Solutions For Tuesday April 8 2025
May 24, 2025
Nyt Mini Crossword Puzzle Solutions For Tuesday April 8 2025
May 24, 2025 -
 Nyt Mini Crossword Answers Today March 13 2025
May 24, 2025
Nyt Mini Crossword Answers Today March 13 2025
May 24, 2025
