New Algorithmic Standards Drive Post-Quantum Cryptography's Growth To Billions By 2030

Table of Contents
The Rise of Quantum Computing and the Urgent Need for PQC
Quantum computing, while still in its nascent stages, poses an existential threat to current cryptographic infrastructure. Quantum computers leverage quantum mechanics to perform calculations far beyond the capabilities of classical computers. This immense processing power allows them to efficiently crack algorithms currently considered secure, such as RSA and Elliptic Curve Cryptography (ECC).
The potential consequences of a successful quantum attack are catastrophic. Imagine a world where financial transactions are easily manipulated, national security secrets are exposed, and patient medical records are vulnerable to theft. The proactive adoption of PQC is not merely a technological advancement; it's a critical necessity to mitigate these future risks and safeguard our digital future.
Understanding the Vulnerability of Existing Cryptography
- RSA: Relies on the difficulty of factoring large numbers. Shor's algorithm, a quantum algorithm, can efficiently solve this problem, rendering RSA vulnerable.
- ECC: Based on the mathematical properties of elliptic curves. Shor's algorithm can also break ECC, compromising its security.
Sensitive data at risk includes:
- Financial transactions and banking information
- Government secrets and classified data
- Personal health records and medical data
- Intellectual property and trade secrets
NIST's Standardization Efforts and Their Impact
The National Institute of Standards and Technology (NIST) has played a pivotal role in guiding the development and standardization of post-quantum cryptography algorithms. Their multi-year process involved rigorous evaluation of various cryptographic schemes based on their security, performance, and implementation characteristics. The selection process rigorously examined algorithms across multiple rounds, ultimately selecting a suite that offers a balance of security and practicality.
NIST's selection process included extensive cryptanalysis, implementation studies, and community feedback. The finalized algorithms represent a significant milestone in securing our digital infrastructure against the threat of quantum computing.
The selected algorithms include:
- CRYSTALS-Kyber: A key encapsulation mechanism (KEM) known for its excellent performance and relatively small key sizes.
- CRYSTALS-Dilithium: A digital signature algorithm offering strong security guarantees.
- FALCON: Another digital signature algorithm, optimized for smaller signature sizes.
- SPHINCS+: A digital signature algorithm based on hash functions, offering strong security properties even against potential future attacks.
Key Characteristics of Standardized PQC Algorithms
- Security Properties: Each algorithm offers strong security against both classical and quantum attacks, based on different mathematical problems that are believed to be resistant to quantum algorithms like Shor's algorithm.
- Performance Characteristics: Performance varies depending on the algorithm and implementation. Some algorithms are optimized for speed, while others prioritize smaller key sizes or signatures.
- Key Sizes: PQC algorithms generally require larger key sizes compared to their classical counterparts.
The diversity in algorithm types is crucial. By standardizing algorithms based on different mathematical foundations, we mitigate the risk of a single breakthrough compromising the entire cryptographic system. This diversity ensures resilience against unexpected future cryptanalytic advances.
Market Growth Projections and Key Drivers
Market research firms project the PQC market to reach billions of dollars by 2030. This significant growth is propelled by several key factors:
- Increasing Awareness of Quantum Computing Threats: As awareness of quantum computing's potential to break current encryption increases, so does the demand for PQC solutions.
- Government Regulations and Mandates: Governments worldwide are increasingly recognizing the need to secure critical infrastructure against quantum attacks, leading to regulatory mandates and incentives for PQC adoption.
- Growing Adoption of PQC in Various Sectors: Industries like finance, healthcare, and government are actively exploring and implementing PQC to protect sensitive data.
Market Segmentation and Opportunities
The PQC market encompasses hardware, software, and services. Significant opportunities exist in developing specialized hardware accelerators for PQC algorithms, creating user-friendly software libraries, and providing professional services for PQC implementation and integration. Investment in research and development of new PQC algorithms and their applications presents lucrative opportunities for both established and emerging technology companies.
Challenges and Future Outlook for PQC Adoption
Despite the promising outlook, several challenges hinder widespread PQC adoption:
- Computational Overhead: PQC algorithms often have higher computational overhead compared to existing algorithms, potentially impacting performance.
- Interoperability Issues: Ensuring seamless interoperability between different PQC implementations requires careful standardization and coordination.
- Skill Gaps in PQC Expertise: There's a significant need for training and development to build a skilled workforce capable of developing, implementing, and managing PQC systems.
The Roadmap for Widespread PQC Adoption
- Education and Training: Invest in education and training programs to develop expertise in PQC.
- Collaboration and Standardization: Foster collaboration between industry, academia, and government to ensure consistent standards and interoperability.
- Technological Advancements: Continue investing in research and development to improve the performance and efficiency of PQC algorithms and their implementation.
Conclusion
The standardization of new algorithms by NIST is a critical catalyst for the rapid expansion of the Post-Quantum Cryptography market, predicted to reach billions by 2030. This growth is driven by the urgent need to safeguard data from the imminent threat of quantum computing. Proactive adoption of PQC is no longer a luxury but a necessity for ensuring long-term data security. Businesses and organizations should start planning for and implementing post-quantum cryptography solutions to ensure the long-term security of their data. Learn more about how to integrate post-quantum cryptography into your systems today, and protect your valuable information from the future of quantum computing.

Featured Posts
-
 Tidak Ada Penempatan Pekerja Migran Di Kamboja Dan Myanmar Pernyataan Resmi Karding
May 13, 2025
Tidak Ada Penempatan Pekerja Migran Di Kamboja Dan Myanmar Pernyataan Resmi Karding
May 13, 2025 -
 Exploring Doom The Dark Ages
May 13, 2025
Exploring Doom The Dark Ages
May 13, 2025 -
 Proposed Texas Muslim City Sparks Governors Outrage And Warning
May 13, 2025
Proposed Texas Muslim City Sparks Governors Outrage And Warning
May 13, 2025 -
 Deciphering The Symbols And Codes In The Da Vinci Code
May 13, 2025
Deciphering The Symbols And Codes In The Da Vinci Code
May 13, 2025 -
 Post Quantum Cryptographys Ascent Timelines Algorithms And Market Projections
May 13, 2025
Post Quantum Cryptographys Ascent Timelines Algorithms And Market Projections
May 13, 2025
Latest Posts
-
 La Protection Civile En Allemagne Faiblesses Passees Et Ambitions Futures
May 13, 2025
La Protection Civile En Allemagne Faiblesses Passees Et Ambitions Futures
May 13, 2025 -
 Plan The Perfect Spring Break For Your Kids Activities And Ideas
May 13, 2025
Plan The Perfect Spring Break For Your Kids Activities And Ideas
May 13, 2025 -
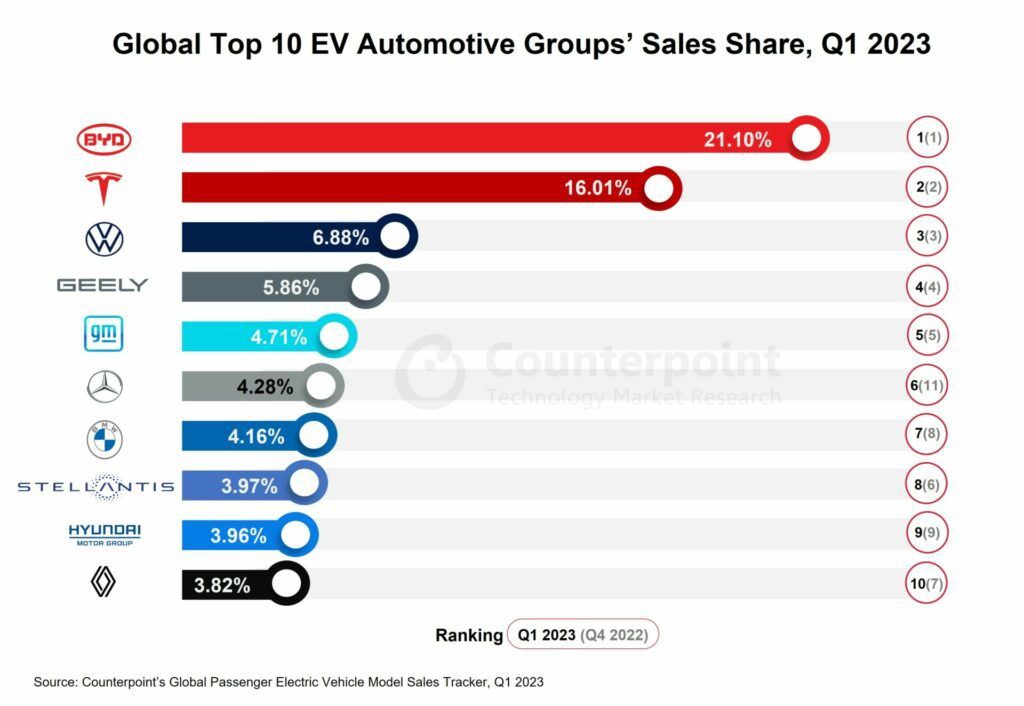 Maluf Fords Decline And Byds Rise In Brazils Ev Market
May 13, 2025
Maluf Fords Decline And Byds Rise In Brazils Ev Market
May 13, 2025 -
 Protection Civile Allemande Modernisation Et Renforcement Face Aux Defis Actuels
May 13, 2025
Protection Civile Allemande Modernisation Et Renforcement Face Aux Defis Actuels
May 13, 2025 -
 Benin Seychelles Croatia Slovakia And Cambodia Welcome Byd Electric Vehicle Expansion
May 13, 2025
Benin Seychelles Croatia Slovakia And Cambodia Welcome Byd Electric Vehicle Expansion
May 13, 2025
