Office365 Data Breach Nets Millions For Hacker, FBI Alleges
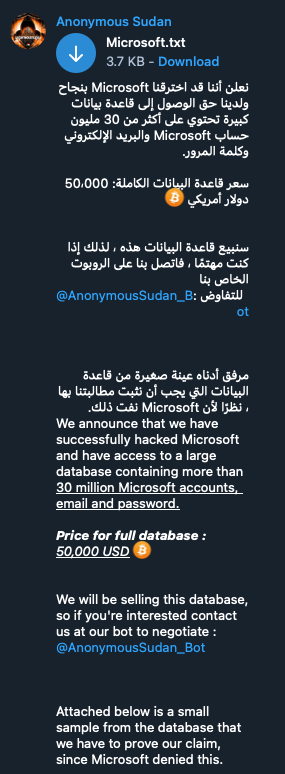
Table of Contents
The Scale of the Office365 Data Breach and its Financial Impact
The FBI alleges that millions of dollars were stolen in this Office365 data breach, though specific figures remain undisclosed pending the ongoing investigation. The impact of this data breach extends far beyond the immediate financial losses. This significant Office365 data loss affected multiple organizations across various sectors, illustrating the widespread vulnerability to this type of cyberattack. The financial consequences are multifaceted:
- Direct Theft: The most immediate loss is the direct theft of funds, potentially through compromised banking information or fraudulent transactions facilitated by stolen data.
- Ransom Payments: If ransomware was involved, organizations may have incurred substantial costs paying ransoms to regain access to their data. The cost of ransomware attacks is a significant factor in overall data breach cost.
- Data Recovery and Remediation: The process of recovering compromised data, investigating the breach's extent, and implementing remediation measures incurs significant costs, involving IT specialists, forensic experts, and legal counsel.
- Reputational Damage: The long-term impact of an Office365 security breach can include severe reputational damage. Loss of customer trust, damaged brand image, and potential legal action can lead to substantial financial losses over time. The impact of data breach on a company's reputation can be devastating.
Methods Used in the Office365 Data Breach and Hacker Tactics
While specifics of the Office365 security breach remain under investigation, several methods could have been employed by the hacker(s). Understanding these tactics is crucial for bolstering your organization's defenses against future attacks. Potential methods include:
- Phishing Campaigns: Sophisticated phishing emails, designed to mimic legitimate communications, could have tricked employees into revealing their Office365 login credentials. Social engineering tactics, preying on human psychology, often prove highly effective in these attacks.
- Exploiting Third-Party App Vulnerabilities: Many organizations integrate third-party apps with Office365. Hackers might have exploited vulnerabilities in these apps to gain unauthorized access to the platform.
- Credential Stuffing: Hackers may have used stolen credentials obtained from previous data breaches against Office365 accounts, attempting to gain access through brute-force methods.
- Multi-Factor Authentication (MFA) Bypass: While MFA is a crucial security measure, determined hackers may try to bypass it through various techniques, including exploiting vulnerabilities or employing social engineering tactics.
- Malware Deployment: Once inside the system, malware could have been used to exfiltrate sensitive data, steal financial information, and potentially deploy ransomware. Advanced persistent threats (APTs) are especially concerning, as they can remain undetected for extended periods.
The FBI Investigation and Legal Ramifications
The FBI's ongoing investigation into this Office365 data breach highlights the seriousness of cybercrime and the commitment of law enforcement to tackling these issues. The legal ramifications for both the hackers and potentially negligent organizations are substantial:
- Criminal Charges: The hackers involved face serious criminal charges, including wire fraud, identity theft, and computer fraud and abuse, carrying lengthy prison sentences and significant fines.
- Civil Litigation: Affected organizations may pursue civil lawsuits against the hackers to recover financial losses.
- Regulatory Fines: Organizations may face substantial fines from regulatory bodies for failing to comply with data protection regulations, such as GDPR or CCPA, if the breach was caused by inadequate security measures.
- Reputational Damage: The legal battles themselves can further damage the reputation of organizations involved, impacting their future business prospects.
Best Practices for Preventing Office365 Data Breaches
The Office365 data breach underscores the critical need for proactive cybersecurity measures. Implementing these best practices can significantly reduce the risk of a similar incident affecting your organization:
- Strong Passwords and Multi-Factor Authentication (MFA): Enforce strong, unique passwords and mandatory MFA for all Office365 accounts.
- Regular Security Awareness Training: Conduct regular training sessions to educate employees about phishing scams, social engineering tactics, and other cyber threats.
- Robust Anti-Phishing and Anti-Malware Solutions: Deploy and maintain up-to-date anti-phishing and anti-malware solutions across all devices and systems.
- Regular Security Audits and Vulnerability Assessments: Conduct periodic security audits and vulnerability assessments to identify and address potential weaknesses in your Office365 security posture.
- Prompt Patching: Keep all software, including Office365 and third-party apps, updated with the latest security patches.
- Data Loss Prevention (DLP) Tools and Encryption: Implement DLP tools to monitor and prevent sensitive data from leaving your organization and use encryption to protect data at rest and in transit.
Conclusion
The Office365 data breach serves as a stark reminder of the ever-present threat of cyberattacks and the potential for significant financial and reputational damage. The FBI investigation underscores the seriousness of these crimes and the importance of proactive security measures. Don't become the next victim. Implement robust security protocols and stay vigilant to protect your organization from an Office365 data breach. Invest in comprehensive cybersecurity solutions and employee training to safeguard your valuable data and mitigate potential financial losses. Learn more about bolstering your Office365 security today.

Featured Posts
-
 College Van Omroepen En Het Herstel Van Vertrouwen Bij De Npo
May 15, 2025
College Van Omroepen En Het Herstel Van Vertrouwen Bij De Npo
May 15, 2025 -
 Toezichthouder Npo Handelt Snel Na Leeflang Gesprek
May 15, 2025
Toezichthouder Npo Handelt Snel Na Leeflang Gesprek
May 15, 2025 -
 Padres Defy Dodgers Strategy Will Their Plan Succeed
May 15, 2025
Padres Defy Dodgers Strategy Will Their Plan Succeed
May 15, 2025 -
 Microsoft Among Top Software Stocks Weathering The Tariff Storm
May 15, 2025
Microsoft Among Top Software Stocks Weathering The Tariff Storm
May 15, 2025 -
 Padres Battle Back To Defeat Cubs
May 15, 2025
Padres Battle Back To Defeat Cubs
May 15, 2025
Latest Posts
-
 1 Kissfms Vont Weekend A Photo Journal April 4th 6th 2025
May 15, 2025
1 Kissfms Vont Weekend A Photo Journal April 4th 6th 2025
May 15, 2025 -
 Vont Weekend Photo Diary April 4 6 2025 103 X
May 15, 2025
Vont Weekend Photo Diary April 4 6 2025 103 X
May 15, 2025 -
 Vont Weekend Photos From April 4th 6th 2025 96 1 Kissfm
May 15, 2025
Vont Weekend Photos From April 4th 6th 2025 96 1 Kissfm
May 15, 2025 -
 Vont Weekend April 4th 6th 2025 In Five Pictures
May 15, 2025
Vont Weekend April 4th 6th 2025 In Five Pictures
May 15, 2025 -
 Vont Weekend Recap April 4th 6th 2025 96 1 Kissfm
May 15, 2025
Vont Weekend Recap April 4th 6th 2025 96 1 Kissfm
May 15, 2025
