Office365 Executive Inboxes Targeted: Millions Stolen In Cybercrime

Table of Contents
The Tactics Behind Office365 Executive Inbox Attacks
Cybercriminals employ increasingly sophisticated methods to compromise Office365 executive inboxes. Understanding these tactics is the first step in effective defense.
Sophisticated Phishing Campaigns
Phishing attacks have evolved far beyond simple spam emails. Targeting executives specifically requires more refined techniques like spear phishing, CEO fraud, and whaling. These attacks leverage social engineering, often impersonating trusted sources or creating a sense of urgency to trick victims into revealing sensitive information or clicking malicious links.
- Examples: Emails appearing to be from a board member requesting urgent wire transfers, forged invoices from a known supplier, or messages containing seemingly legitimate links leading to phishing websites.
- Social Engineering: Attackers build rapport, exploit relationships, and leverage inside information to gain the victim's trust.
- Success Rate: Statistics show a high success rate for sophisticated phishing campaigns targeting executives due to their perceived authority and lack of awareness about the risks. A recent study showed that over 60% of executives fall victim to phishing attempts at least once a year.
Exploiting Weak Passwords and Security Gaps
Many attacks exploit weak passwords and vulnerabilities in Office365 configurations. The lack of robust security practices, like multi-factor authentication (MFA), further increases the risk.
- Common Password Weaknesses: Using easily guessable passwords, reusing passwords across multiple accounts, and failing to change passwords regularly.
- Importance of Strong Passwords and Password Managers: Utilize strong, unique passwords for each account and consider using a password manager to simplify this process.
- Benefits of MFA: MFA adds an extra layer of security, requiring a second verification factor (e.g., a code sent to a mobile phone) beyond the password, making it significantly harder for attackers to gain access even if they obtain the password.
- Compromised Credentials: Stolen credentials from other platforms or breaches are often used to access executive inboxes, highlighting the importance of strong overall security practices.
Malware and Ransomware Deployment
Once access is gained, attackers often deploy malware or ransomware. Ransomware encrypts sensitive data, demanding a ransom for its release. Malware can steal data, disrupt operations, and create further vulnerabilities.
- Types of Malware/Ransomware: Various types exist, from simple keyloggers to sophisticated ransomware like Ryuk and Conti.
- Methods of Delivery: Malicious attachments in emails, links redirecting to compromised websites, or exploiting vulnerabilities in outdated software.
- Impact on Business Operations: Data loss, operational downtime, financial losses from ransom payments, and reputational damage.
The Devastating Consequences of a Compromised Executive Inbox
The consequences of a compromised executive inbox extend far beyond the immediate financial losses. The impact on a business can be severe and long-lasting.
Financial Losses
Data breaches from compromised executive inboxes result in substantial financial losses. These include:
- Ransom payments: Organizations often pay hefty ransoms to regain access to their encrypted data.
- Legal fees: Investigations, legal battles, and regulatory fines can add significantly to the cost.
- Reputational damage: Loss of customer trust, reduced investor confidence, and difficulty attracting new talent.
- Average Cost of a Data Breach: The cost of data breaches averages millions of dollars, depending on factors such as the size of the organization and the type of data compromised.
Reputational Damage
The reputational damage following a data breach can be substantial and long-lasting:
- Negative media coverage: A data breach can lead to negative news coverage, harming the company's image and public perception.
- Loss of market share: Customers may switch to competitors following a loss of trust.
- Difficulty attracting talent: Top candidates may avoid companies perceived as having weak security.
Legal and Regulatory Compliance Issues
Organizations face significant legal and regulatory consequences following data breaches:
- GDPR, CCPA, and other regulations: Non-compliance can result in hefty fines and lawsuits.
- Potential penalties: These can be substantial, running into millions of dollars depending on the severity of the breach and the jurisdiction.
Protecting Your Office365 Executive Inboxes
Protecting executive inboxes requires a multi-layered approach that combines technical and human elements.
Strengthening Password Security
Implementing strong password policies and using MFA are crucial:
- Strong passwords: Encourage the use of complex, unique passwords for each account.
- Password managers: Utilize password managers to generate and securely store complex passwords.
- Multi-factor authentication (MFA): Make MFA mandatory for all users, especially executives.
Advanced Threat Protection
Leverage Office365's advanced threat protection features:
- Anti-phishing: Employ advanced anti-phishing techniques to detect and block malicious emails.
- Anti-malware: Implement robust anti-malware protection to prevent malware infections.
- Data Loss Prevention (DLP): Use DLP tools to monitor and prevent sensitive data from leaving the organization's network.
Security Awareness Training
Regular security awareness training is essential for all employees:
- Phishing simulations: Conduct regular phishing simulations to educate employees on identifying and avoiding phishing attempts.
- Security best practices: Provide training on security best practices, including password management, safe browsing habits, and how to identify malicious emails.
Regular Security Audits and Vulnerability Assessments
Regular security audits and penetration testing are crucial:
- Identify vulnerabilities: These assessments identify security weaknesses in the Office365 environment.
- Proactive measures: Address vulnerabilities promptly to prevent potential attacks.
Conclusion
Protecting Office365 executive inboxes from cyberattacks is paramount. The tactics employed by cybercriminals are sophisticated, and the consequences of a successful attack can be devastating. By implementing robust security measures, including strong password policies, MFA, advanced threat protection, security awareness training, and regular security audits, organizations can significantly reduce their risk of falling victim to Office365 executive inbox cybercrime. Don't wait until it's too late; take immediate action to secure your Office365 executive inboxes and protect your business. For more information on Office365 security best practices, refer to Microsoft's security resources and consider consulting with a cybersecurity expert.

Featured Posts
-
 Federal Investigation Uncovers Millions Lost In Office365 Executive Hacks
Apr 23, 2025
Federal Investigation Uncovers Millions Lost In Office365 Executive Hacks
Apr 23, 2025 -
 Vetrine Spaccate 200 Manifestanti Protestano Contro Gli Attacchi Ai Ristoranti Palestinesi
Apr 23, 2025
Vetrine Spaccate 200 Manifestanti Protestano Contro Gli Attacchi Ai Ristoranti Palestinesi
Apr 23, 2025 -
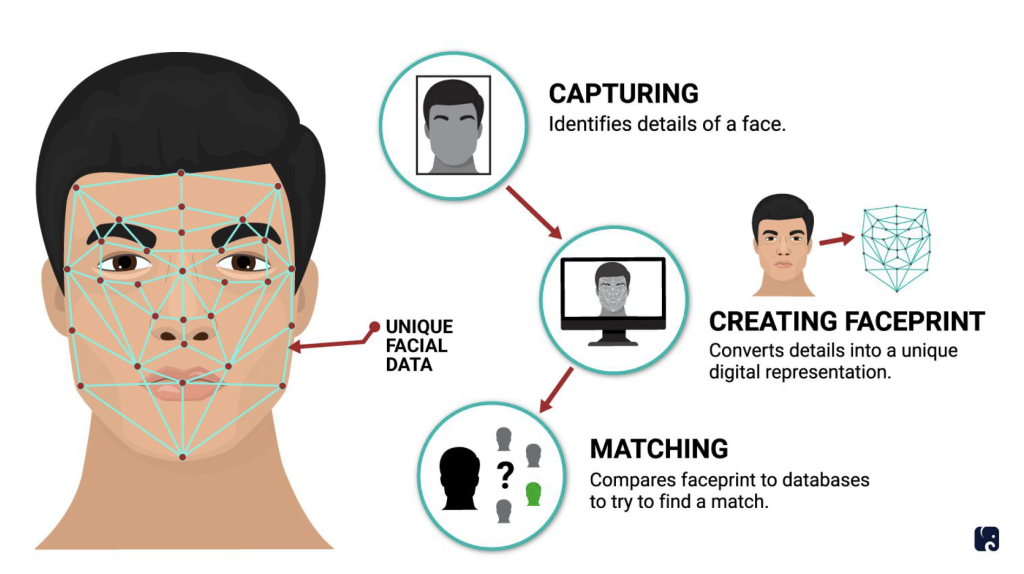 Target Fields Go Ahead Entry System How Facial Recognition Works
Apr 23, 2025
Target Fields Go Ahead Entry System How Facial Recognition Works
Apr 23, 2025 -
 The Oracles Apple Exit Understanding Buffetts Timing And Next Steps
Apr 23, 2025
The Oracles Apple Exit Understanding Buffetts Timing And Next Steps
Apr 23, 2025 -
 Ryujinx Emulator Development Halted Nintendos Involvement Confirmed
Apr 23, 2025
Ryujinx Emulator Development Halted Nintendos Involvement Confirmed
Apr 23, 2025
Latest Posts
-
 Us Eu Trade Dispute French Minister Advocates For Increased Retaliation
May 10, 2025
Us Eu Trade Dispute French Minister Advocates For Increased Retaliation
May 10, 2025 -
 Trade Tensions French Minister Seeks Tougher Eu Stance On Us Tariffs
May 10, 2025
Trade Tensions French Minister Seeks Tougher Eu Stance On Us Tariffs
May 10, 2025 -
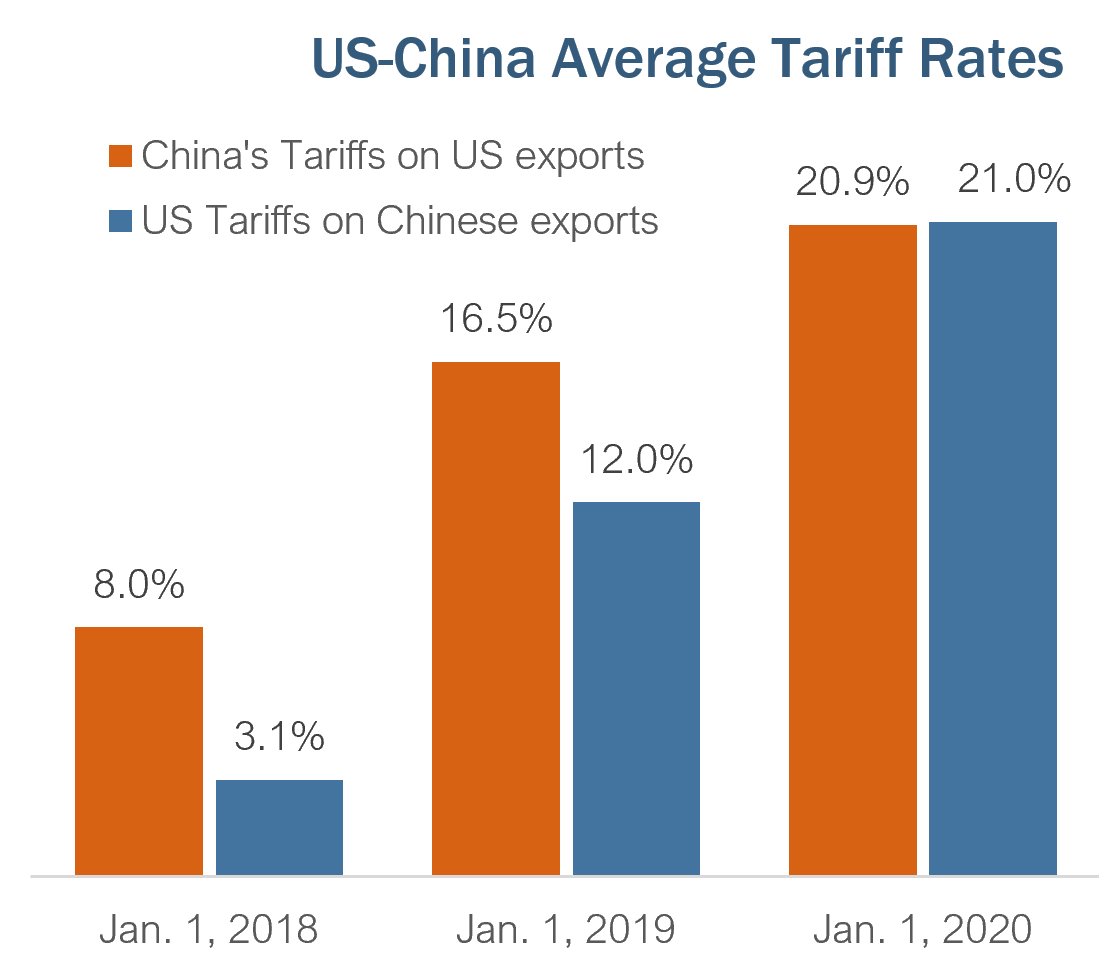 French Minister Eu Must Do More To Counter Us Tariffs
May 10, 2025
French Minister Eu Must Do More To Counter Us Tariffs
May 10, 2025 -
 Stronger Eu Response To Us Tariffs Demanded By French Minister
May 10, 2025
Stronger Eu Response To Us Tariffs Demanded By French Minister
May 10, 2025 -
 France Pushes For Enhanced Eu Response To Us Trade Tariffs
May 10, 2025
France Pushes For Enhanced Eu Response To Us Trade Tariffs
May 10, 2025
