Federal Investigation: Massive Office365 Data Breach Nets Millions

Table of Contents
Scale and Scope of the Office365 Data Breach
The Office365 data breach represents a significant cybersecurity event, affecting an estimated 5 million users across various sectors. The compromised data includes a wide range of sensitive information, from emails and documents containing confidential business strategies to personal details like financial records and customer lists. The sheer volume of data compromised is staggering, making this one of the largest Office365 data breaches in recent history. The geographical spread is also extensive, with reports indicating affected users in North America, Europe, and Asia. The initial timeline of the breach remains under investigation, but early indications suggest the compromise may have been ongoing for several months before detection.
- Estimated number of affected users: 5 million+
- Types of data compromised: Emails, documents, financial data, customer lists, intellectual property, personal information.
- Regions and organizations most impacted: North America, Europe, Asia; various industries including finance, healthcare, and education.
- Initial timeline of the breach: Still under investigation, but potentially spanning several months.
The Federal Investigation: Key Findings and Actions
The federal investigation into this Office365 data breach involves multiple agencies, including the FBI and the Cybersecurity and Infrastructure Security Agency (CISA). Their primary focus is on identifying the perpetrators, determining the precise method of the breach (e.g., phishing attacks, exploiting known vulnerabilities), and assessing the full extent of the damage. The investigation is examining potential violations of federal laws related to data security and cybercrime. Legal ramifications for those responsible could include significant fines and potential criminal charges. The expected timeline for the investigation's completion remains unclear, but authorities are working diligently to bring the perpetrators to justice.
- Agencies involved in the investigation: FBI, CISA, and potentially others.
- Focus of the investigation: Identifying perpetrators, determining breach method, assessing damage, and pursuing legal action.
- Potential legal ramifications for those responsible: Substantial fines and criminal charges.
- Expected timeline for the investigation's completion: Currently unknown.
Vulnerabilities Exploited and Lessons Learned
While the exact vulnerabilities exploited in this Office365 data breach are still under investigation, preliminary findings suggest that several common attack vectors may have been employed. These include sophisticated phishing attacks targeting employees with malicious emails containing malware, the exploitation of known vulnerabilities in older versions of Office365 software, and possibly weak password security practices. The lack of robust multi-factor authentication (MFA) may have also played a significant role. This highlights the crucial need for organizations to prioritize proactive cybersecurity measures.
- Identified vulnerabilities in Office365 security: Weak password security, lack of MFA, outdated software, susceptibility to phishing attacks.
- Attack vectors used by the perpetrators: Phishing emails, malware, exploiting known vulnerabilities.
- Recommendations for improving Office365 security: Implementing MFA, enforcing strong password policies, regular security audits, deploying updated software, employee cybersecurity training.
Best Practices for Protecting Your Office365 Data
Protecting your Office365 data requires a multi-layered approach. Implementing the following best practices can significantly reduce your risk of falling victim to a data breach:
- Implement strong password policies and multi-factor authentication (MFA): Enforce complex passwords and require MFA for all accounts.
- Conduct regular security awareness training for employees: Educate employees about phishing scams, malware, and other cybersecurity threats.
- Keep Office365 software and applications updated: Regularly install security patches and updates to address known vulnerabilities.
- Regularly back up your data: Implement a robust data backup and recovery plan to minimize data loss in the event of a breach.
- Develop and test an incident response plan: Having a pre-defined plan in place will help your organization respond quickly and effectively to a security incident.
Conclusion
The massive Office365 data breach affecting millions underscores the critical importance of robust cybersecurity practices. The ongoing federal investigation highlights the severe consequences of inadequate security measures and the need for proactive prevention strategies. By implementing the best practices outlined in this article, organizations and individuals can significantly reduce their vulnerability to similar attacks. Protect your organization from an Office365 data breach; strengthen your Office365 security today. Learn more about Office365 data breach prevention strategies and ensure your data remains secure.

Featured Posts
-
 Samsonova Ustupila Aleksandrovoy V Shtutgarte Itogi Pervogo Kruga
May 23, 2025
Samsonova Ustupila Aleksandrovoy V Shtutgarte Itogi Pervogo Kruga
May 23, 2025 -
 European Stock Markets Today Midday Update And Pmi Analysis
May 23, 2025
European Stock Markets Today Midday Update And Pmi Analysis
May 23, 2025 -
 Dylan Dreyers Postpartum Body Transformation On The Today Show
May 23, 2025
Dylan Dreyers Postpartum Body Transformation On The Today Show
May 23, 2025 -
 Remont Pivdennogo Mostu Pidryadniki Protses Ta Finansuvannya
May 23, 2025
Remont Pivdennogo Mostu Pidryadniki Protses Ta Finansuvannya
May 23, 2025 -
 Blue Origin Scraps Rocket Launch Due To Vehicle Subsystem Problem
May 23, 2025
Blue Origin Scraps Rocket Launch Due To Vehicle Subsystem Problem
May 23, 2025
Latest Posts
-
 Dow Jones Index Cautious Climb Continues After Strong Pmi Data
May 24, 2025
Dow Jones Index Cautious Climb Continues After Strong Pmi Data
May 24, 2025 -
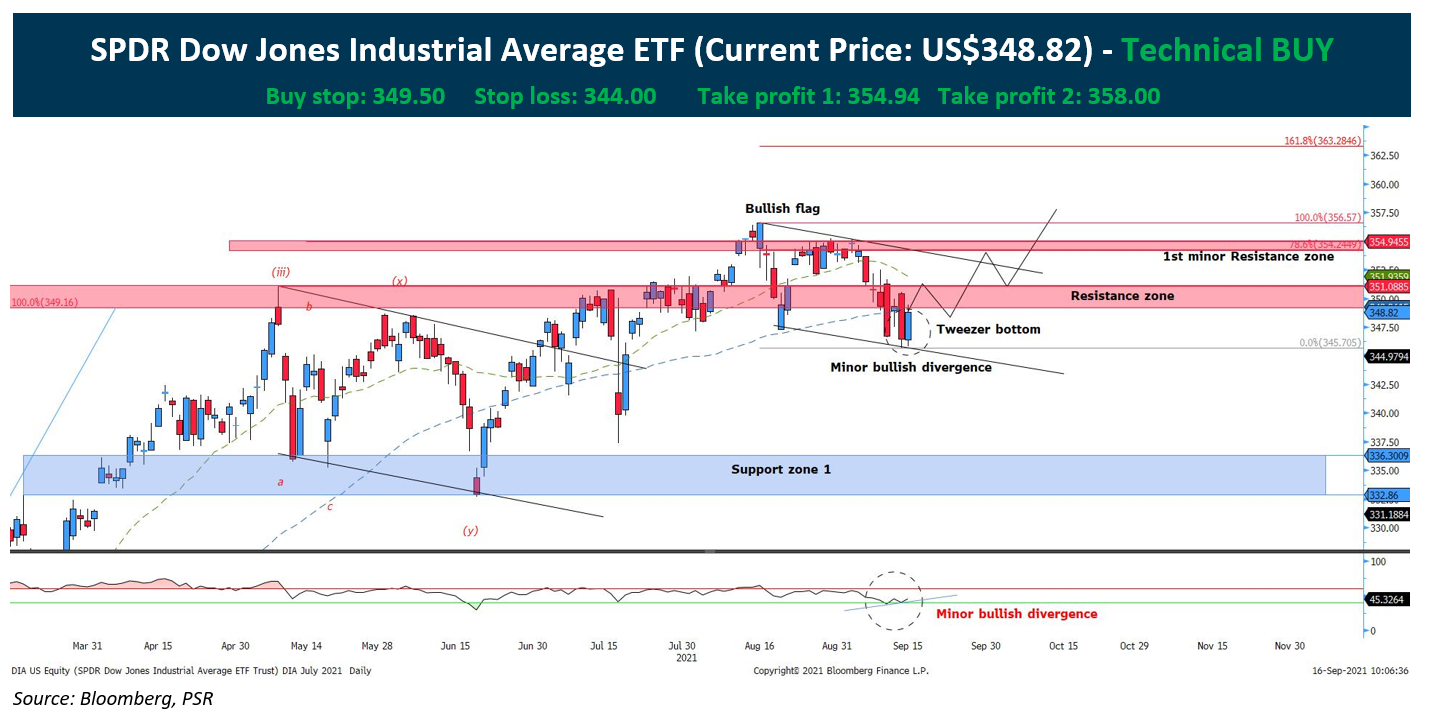 Amundi Dow Jones Industrial Average Ucits Etf Daily Nav And Its Implications
May 24, 2025
Amundi Dow Jones Industrial Average Ucits Etf Daily Nav And Its Implications
May 24, 2025 -
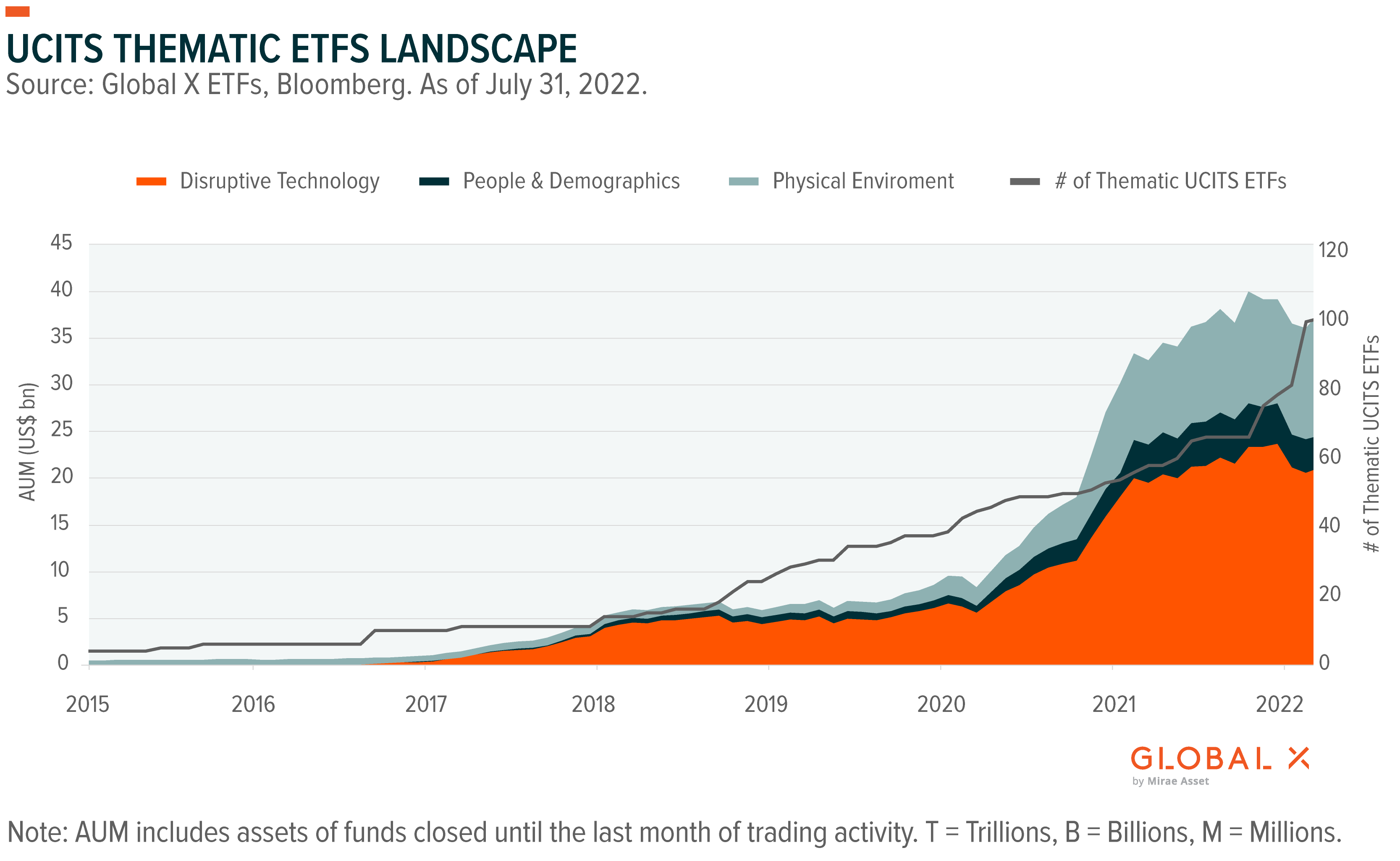 Amundi Dow Jones Industrial Average Ucits Etf A Guide To Net Asset Value Nav
May 24, 2025
Amundi Dow Jones Industrial Average Ucits Etf A Guide To Net Asset Value Nav
May 24, 2025 -
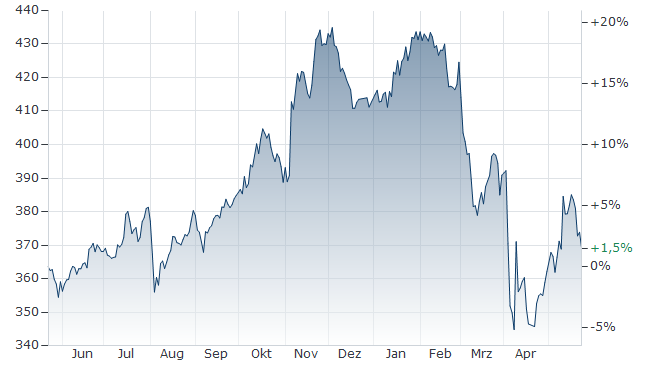 Net Asset Value Nav Of Amundi Dow Jones Industrial Average Ucits Etf
May 24, 2025
Net Asset Value Nav Of Amundi Dow Jones Industrial Average Ucits Etf
May 24, 2025 -
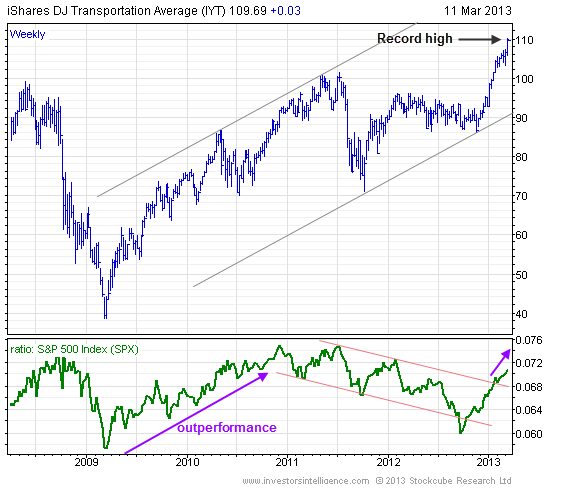 Amundi Dow Jones Industrial Average Ucits Etf Understanding Net Asset Value Nav
May 24, 2025
Amundi Dow Jones Industrial Average Ucits Etf Understanding Net Asset Value Nav
May 24, 2025
