Millions Lost: Inside The Office365 Executive Account Hacking Scandal

Table of Contents
The Modus Operandi: How Executive Office365 Accounts Are Compromised
Cybercriminals employ increasingly sophisticated tactics to compromise executive Office365 accounts, leading to significant data breaches and financial losses. Understanding these methods is the first step in effective prevention.
Spear Phishing and Highly Targeted Attacks
Spear phishing is a cornerstone of many successful Office365 hacking attempts. These attacks aren't random; they're highly personalized, using information gleaned from social media, company websites, and other public sources to craft convincing emails.
- Examples of effective phishing techniques: Mimicking legitimate emails from trusted sources (e.g., a known vendor or colleague), creating a sense of urgency to pressure the recipient into acting quickly, and using sophisticated spoofing techniques to make the email appear authentic.
- Common targets: CEOs, CFOs, and other high-level executives are prime targets because they often have access to sensitive financial information and decision-making power. Their compromised accounts provide direct access to critical systems and data.
- Social engineering: Attackers leverage social engineering tactics to manipulate victims into clicking malicious links or downloading infected attachments. This involves building trust and exploiting human psychology.
Exploiting Weak Passwords and Multi-Factor Authentication Gaps
Weak or reused passwords remain a significant vulnerability. Even with advanced security measures in place, weak passwords can be easily cracked, giving attackers entry to Office365 accounts. The lack of robust multi-factor authentication (MFA) further exacerbates this problem.
- Statistics on password breaches: Millions of credentials are compromised annually through password breaches. Weak passwords are easily guessed or cracked using brute-force attacks.
- Importance of strong, unique passwords: Use strong, unique passwords for every account. Consider using a password manager to generate and securely store these passwords.
- Necessity of robust MFA implementation: MFA adds an extra layer of security, requiring a second form of verification (e.g., a code sent to your phone) beyond just a password. Enforce MFA across all Office365 accounts to significantly reduce the risk of unauthorized access.
Malicious Software and Backdoors
Once initial access is gained, attackers often deploy malware to maintain persistent access and control over the compromised Office365 account. This malware can range from keyloggers to ransomware.
- Examples of malware used: Keyloggers record keystrokes, stealing sensitive information like passwords and credit card details. Ransomware encrypts data, demanding a ransom for its release. Backdoors provide persistent access even after the initial infection vector is removed.
- Methods of infiltration: Malware can be delivered through malicious attachments, infected links, or software vulnerabilities.
- Challenges of detecting and removing persistent threats: Detecting and removing persistent threats requires advanced security tools and expertise. Regular security audits and vulnerability assessments are crucial.
The Devastating Consequences: Financial and Reputational Damage
The consequences of successful Office365 executive account hacking extend far beyond the initial compromise. The financial and reputational damage can be catastrophic.
Financial Losses from Fraudulent Transactions and Ransomware Attacks
The financial impact of these attacks is substantial. Compromised accounts can be used to authorize fraudulent wire transfers, initiate ransomware attacks, and steal sensitive financial data.
- Examples of fraudulent wire transfers: Attackers can impersonate executives to authorize large payments to fraudulent accounts.
- Ransomware demands: Ransomware attacks can cripple operations and demand significant sums for data recovery.
- Overall financial burden: The financial burden on affected companies includes direct losses, remediation costs, and potential legal fees.
Reputational Damage and Loss of Customer Trust
Data breaches and financial losses severely damage a company's reputation and erode customer trust. This can lead to long-term negative consequences.
- Negative media coverage: News of a data breach can lead to widespread negative media attention, damaging the company's image.
- Loss of investor confidence: Investors may lose confidence in the company, leading to decreased stock value and difficulty securing future funding.
- Damage to brand image: A damaged reputation can lead to decreased customer loyalty and difficulty attracting new customers.
Legal and Regulatory Compliance Issues
Data breaches often trigger legal and regulatory compliance issues, resulting in significant fines and legal battles.
- GDPR, CCPA, and other relevant regulations: Non-compliance with data protection regulations like GDPR and CCPA can lead to substantial fines.
- Potential lawsuits and penalties: Affected individuals and businesses may file lawsuits seeking compensation for damages.
Protecting Your Organization: Best Practices for Office365 Security
Protecting your organization from Office365 hacking requires a multi-layered approach incorporating robust security measures and employee training.
Implementing Robust Multi-Factor Authentication (MFA)
MFA is a critical security layer. It adds an extra step to the login process, making it much harder for attackers to access accounts even if they have a password.
- Different types of MFA: Options include one-time passwords (OTP) sent via SMS or email, biometric authentication (fingerprint or facial recognition), and security keys.
- How to enforce MFA across the organization: Implement MFA across all Office365 accounts, prioritizing executive accounts.
Security Awareness Training for Employees
Employee training is paramount in preventing phishing attacks. Educated employees are less likely to fall victim to malicious emails.
- Regular phishing simulations: Conduct regular simulated phishing attacks to test employee awareness and reinforce training.
- Educating employees about recognizing and reporting suspicious emails: Train employees on how to identify suspicious emails, links, and attachments.
Utilizing Advanced Security Features in Office365
Office365 offers several advanced security features to enhance protection. Leveraging these features is crucial for comprehensive security.
- Specific Office365 security features: Advanced Threat Protection (ATP), Data Loss Prevention (DLP), and Microsoft Defender for Office 365.
- How they can help prevent attacks: These features can detect and block malicious emails, prevent sensitive data from leaving the organization, and monitor user activity for suspicious behavior.
Regular Security Audits and Vulnerability Assessments
Proactive security measures are essential. Regularly scheduled security audits and vulnerability assessments identify and address weaknesses before they can be exploited.
- The frequency of audits: Security audits should be conducted regularly, ideally on a quarterly or annual basis.
- Types of assessments: Penetration testing simulates real-world attacks to identify vulnerabilities, while vulnerability scanning identifies potential weaknesses in systems and software.
Conclusion
The escalating frequency and sophistication of Office365 executive account hacking incidents underscore the critical need for robust cybersecurity measures. Millions have already been lost due to these attacks, and the consequences extend far beyond financial losses, impacting reputation, legal compliance, and overall business stability. By implementing strong passwords, robust multi-factor authentication, comprehensive security awareness training, and leveraging the advanced security features within Office365, organizations can significantly reduce their vulnerability to these devastating attacks. Don't become another statistic—proactively strengthen your Office365 security today. Learn more about protecting your executive accounts and preventing millions from being lost due to Office365 hacking.

Featured Posts
-
 Dramatic Escape Family Flees Manhole Explosion
Apr 23, 2025
Dramatic Escape Family Flees Manhole Explosion
Apr 23, 2025 -
 Scrutin Legislatif Allemand A J 6 Les Derniers Enjeux
Apr 23, 2025
Scrutin Legislatif Allemand A J 6 Les Derniers Enjeux
Apr 23, 2025 -
 L Appreciation Clientele Infotel Temoignages Et Valeur Ajoutee
Apr 23, 2025
L Appreciation Clientele Infotel Temoignages Et Valeur Ajoutee
Apr 23, 2025 -
 Blue Origins Setbacks A More Significant Failure Than Katy Perrys Recent Struggles
Apr 23, 2025
Blue Origins Setbacks A More Significant Failure Than Katy Perrys Recent Struggles
Apr 23, 2025 -
 Extreme Price Hike Concerns At And T On Broadcoms V Mware Acquisition
Apr 23, 2025
Extreme Price Hike Concerns At And T On Broadcoms V Mware Acquisition
Apr 23, 2025
Latest Posts
-
 Stock Market Today Sensex And Nifty Surge Adani Ports Gains Eternal Declines
May 10, 2025
Stock Market Today Sensex And Nifty Surge Adani Ports Gains Eternal Declines
May 10, 2025 -
 Is It Too Late To Invest In Palantir Stock Before The Predicted 40 Rise In 2025
May 10, 2025
Is It Too Late To Invest In Palantir Stock Before The Predicted 40 Rise In 2025
May 10, 2025 -
 Sensex Soars 500 Points Nifty Above 18400 Adani Ports And Other Stock Market Updates
May 10, 2025
Sensex Soars 500 Points Nifty Above 18400 Adani Ports And Other Stock Market Updates
May 10, 2025 -
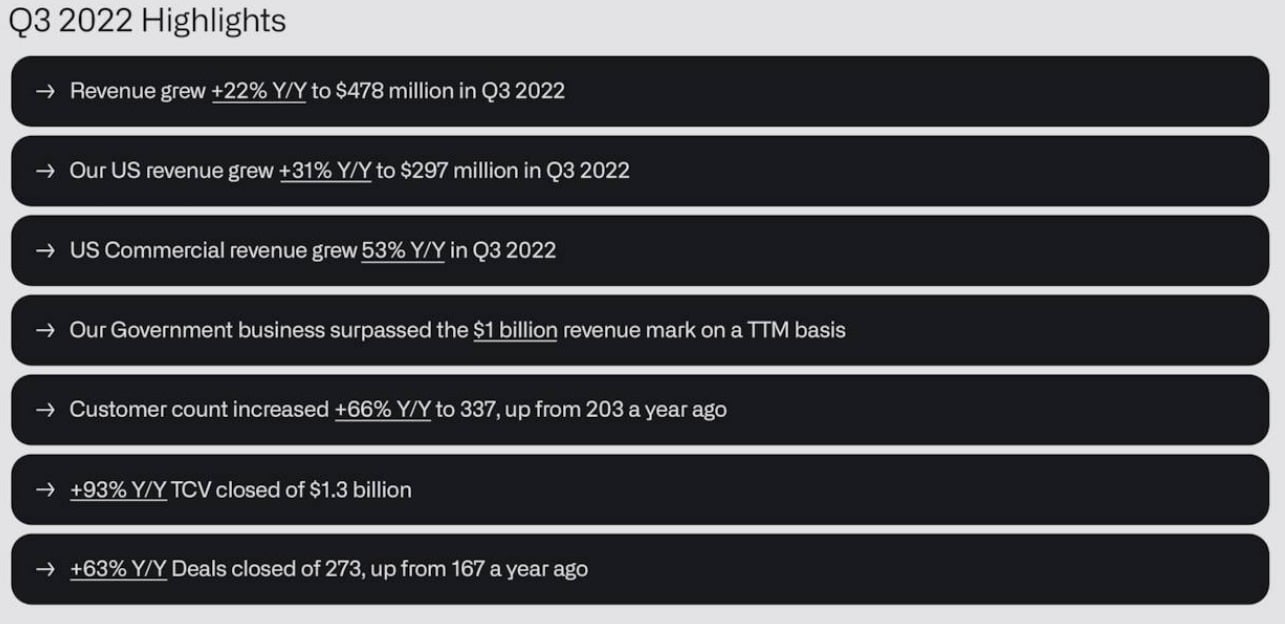 Analyzing The 40 Palantir Stock Price Prediction For 2025 A Detailed Guide
May 10, 2025
Analyzing The 40 Palantir Stock Price Prediction For 2025 A Detailed Guide
May 10, 2025 -
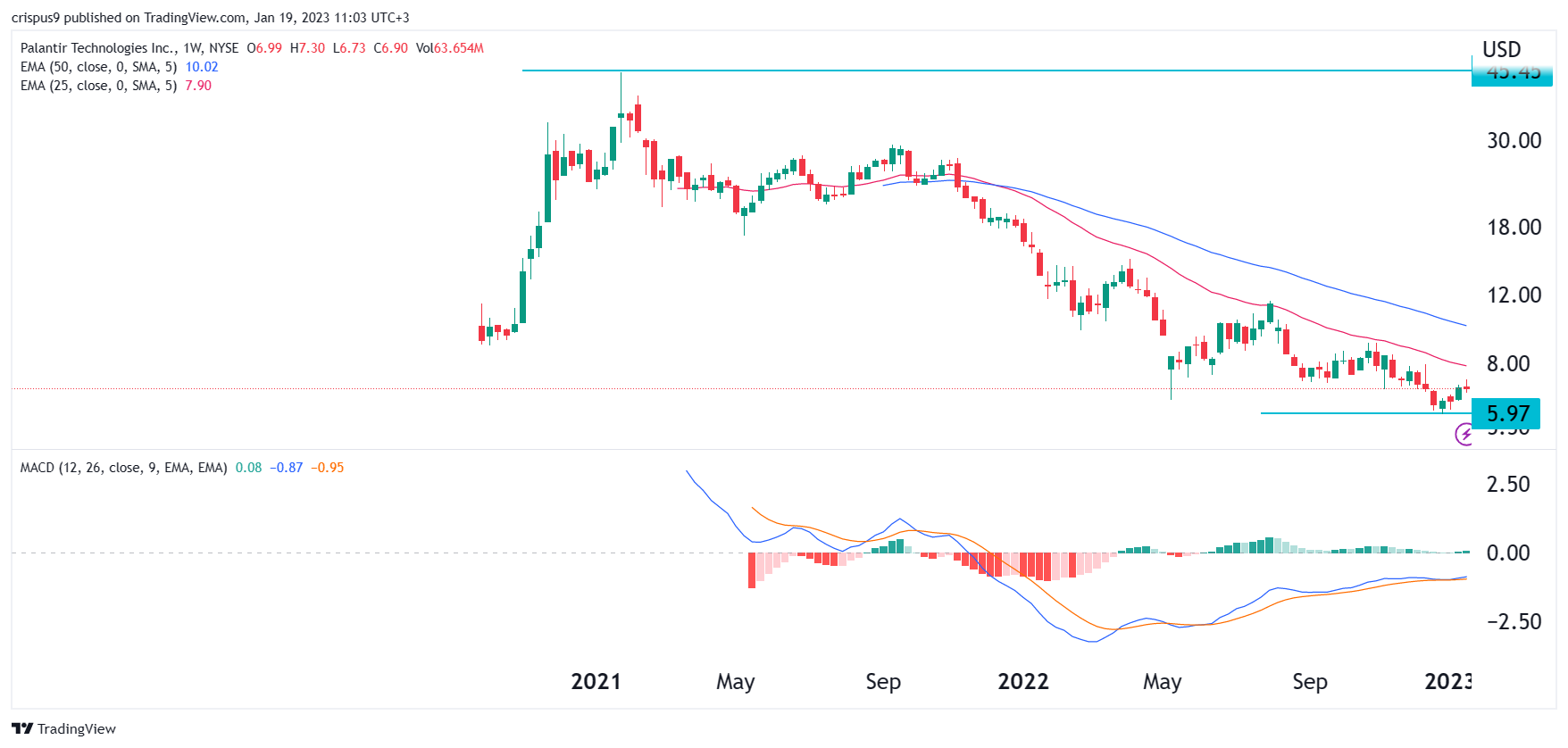 Palantir Stock Weighing The Risks And Rewards Of A Potential 40 Jump In 2025
May 10, 2025
Palantir Stock Weighing The Risks And Rewards Of A Potential 40 Jump In 2025
May 10, 2025
